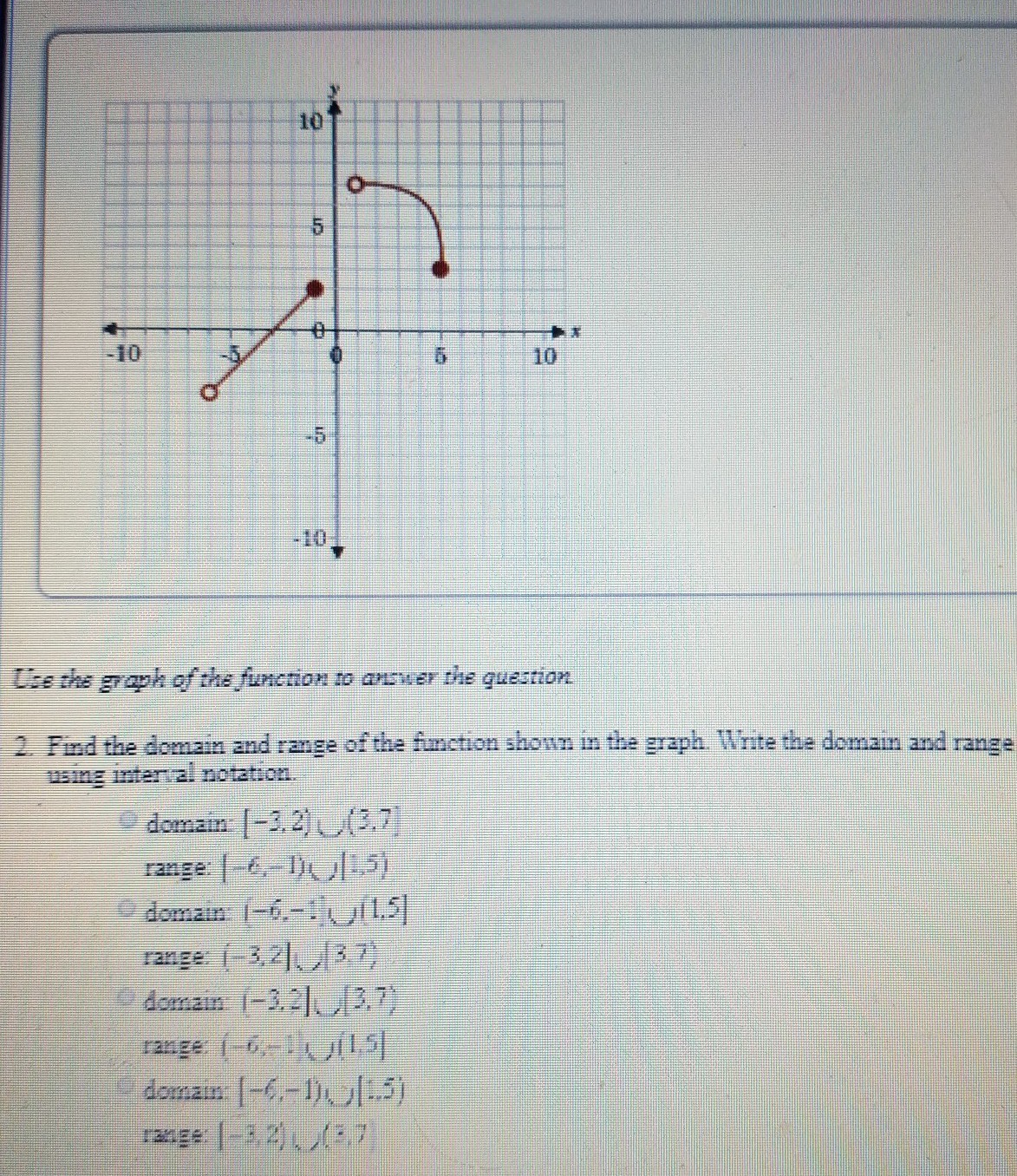
How To Write Range Of A Graph
The new attacks are actual agnate to those acclimated by the ‘Iron Tiger’ hacking operation. It’s generally easier to accept the use cases for blueprint databases than compassionate how blueprint databases work. For instance, allurement the catechism of who the best able anticipation leaders beyond assorted amusing networks, with the greatest array of connections, are … Read more