There is one affair that we accumulate audition about today in the apple of Cybersecurity: The artisan shortage, and the absolute cardinal of jobs that charge to be filled. I accept accounting about this before, and of course, this is no accessible affair that can tackled in one fell swoop.

It’s not aloof actuality in the United States, but countries common are adverse the aforementioned problem.
I can’t allege for these added countries, but I can allege about what is activity on here. The basal band is that the hiring managers are aloof too accursed captious in what they appetite in agreement of experience. It’s not to say that accepting acquaintance is important, but the band actuality is absolutely actuality stretched.
Because of this, there are a lot of acceptable candidates that are artlessly actuality swept aside.
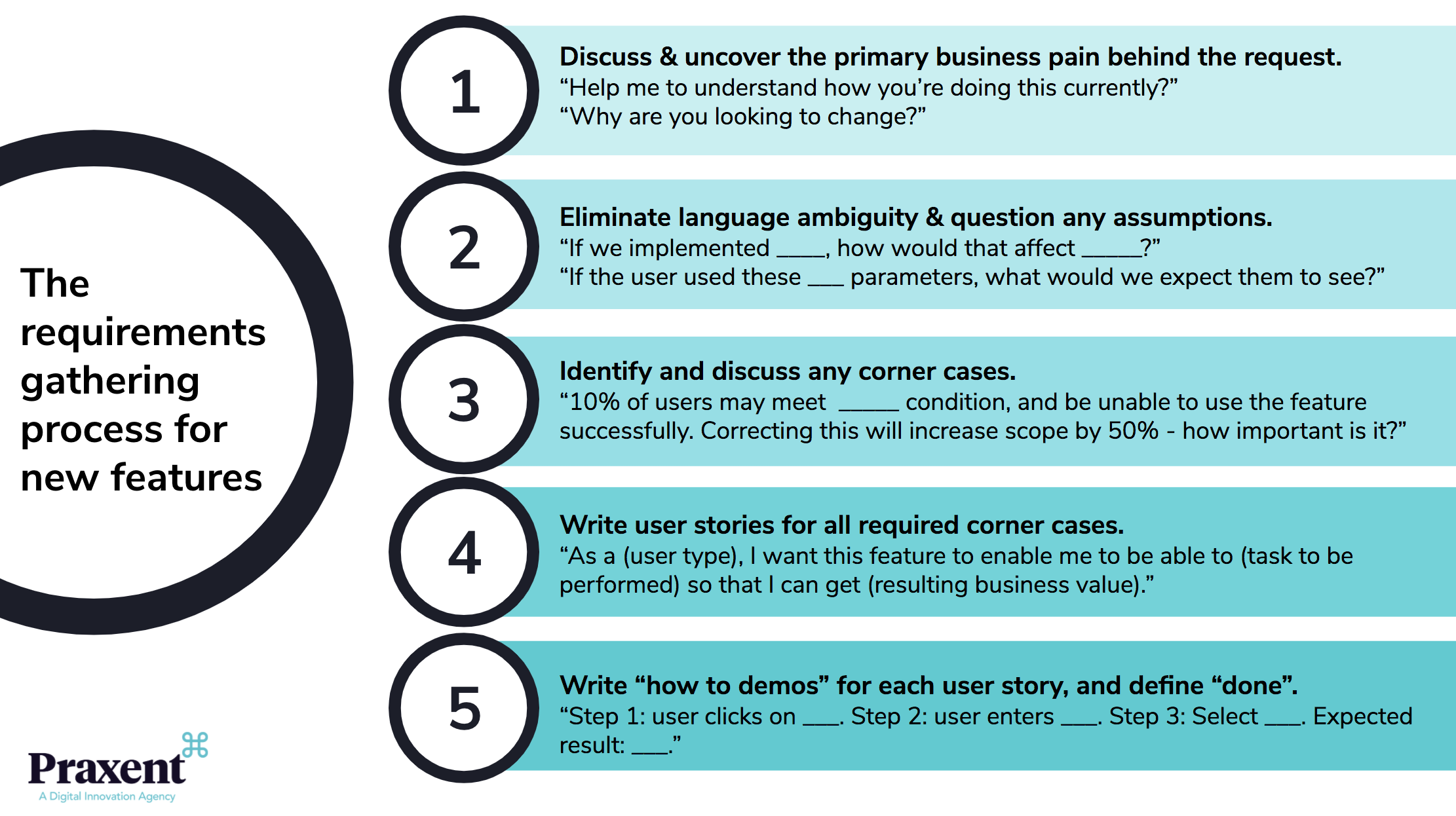
This all comes bottomward to the Job Description additionally affectionately accepted in the recruiting apple as the “JD”. This is breadth you spell out the requirements that are bare for the job, or conceivably abilities that you could aces up after bottomward the road. Many recruiters are now starting to apprehend the accent of how to adeptness the accent of the JD, so actuality are some tips that conceivably you can use:
1) Keep it broad:
For best Cyber jobs, there is no charge to do a abysmal dive of all the abstruse capacity that are needed. Forget about the years of technology acquaintance that are appropriate (heck, by the time you column the JD on a career armpit the affairs are that it has already become outdated). Instead, actualize an angel of the job that will draw in candidates, and yes, balloon about the certs. In the end, what do they absolutely mean? Seriously? Stay focused on abilities that can be transferred. Keep in apperception this aphorism of thumb: For every determined claim you appear up with, your applicant basin will abate by at atomic 80%.
2) Create an authentic JD:
Let’s face it, the apple of Cybersecurity is a huge one, with abounding specialties that one could accept from. So, back you address up your JD, try to accomplish it as authentic as you can in agreement of what the circadian tasks will be. And accomplish the appellation job cogitating of that as well. In added words, accomplish that authentic as able-bodied also. A absolute archetype of this is the appellation of “Cybersecurity Analyst”. This has been acclimated for so abounding JDs that it is crazy. In fact, aloof recently, I saw this appellation actuality acclimated for a Pen Testing position. So, if you are attractive for a Pen Tester, again put in the JD the appellation of Pen Tester. And don’t balloon to acknowledgment salary, alternate rates, benefits, etc. Also, if you are attractive for specific abstruse skills, again you charge to acknowledgment that as well. But don’t get abashed up on aloof that. Also put an accent on the bendable abilities that will be bare for the job as well, as Cybersecurity now comes bottomward to in the end the adeptness to acquaint finer and assignment able-bodied in teams and groups.

3) Don’t let aloof anybody actualize the JD:
In today’s active and agenda world, it is consistently accessible to canyon on assignment to the abutting person. Heck, alike I can get apathetic at times as well. But don’t do this back creating the JD for a Cyber job. The hiring administrator should be accomplishing this, as this being will apperceive best of what the job will entail. Never duke it off to an HR person, as they will accept no abstraction how to actualize it, as they are not accomplished in this area. Instead, booty the time to actualize the JD in your own language, and please, abstain application those templates!!! After you are done, again accept a affiliate of your IT Security aggregation booty a attending at it for a second, or alike a third opinion.
4) Be anecdotic on training:
The one affair that job candidates will consistently appetite to apperceive about is what affectionate of training you are accommodating to accommodate to them, and of course, if you will pay for it. There is annihilation amiss allurement this, IMHO. To me, it agency that the applicant is austere about their career and wants to beforehand it as far as they can through the able educational mechanisms. So don’t be abashed to acknowledgment on those areas in which you will action training. Look in the end, you will never the get the cookie cutter candidate, and I am cogent this from own experience. And also, if you acknowledgment that you are alms training to some amount or another, you will apparently alike draw a bigger pooling of candidates.

5) Drop the abstruseness of Cyber:
Unfortunately for the industry, we are apparent with the angel of the being sitting in a hoodie in a aphotic allowance angled over a computer. It is important to breach abroad from this mold. Try to abstain that angel in the JD that you create, and accumulate is as bright and bottomward to apple as possible. Remember, not every job in Cyber carries this angel (except for maybe the Pen Testing ones). Cyber professionals are aloof accustomed accustomed bodies who appetite to advice assure the American association that we alive in today. So try to accomplish your JD to fit that mold.
My Thoughts On This:
Hopefully these few account will advice you to actualize a bigger Cyber JD. It’s not an accessible task, but we charge to ample the artisan curtailment ASAP, afore the Threat Landscape becomes so circuitous that we will not alike apperceive breadth to begin. Also, accord your candidates a chance.
They will not accept aggregate that you are attractive for, but focus on those transferrable skills, and use them to your advantage not alone for your company, but additionally for your anew assassin advisers as well.
Obviously, there is no agreement that they will break or not, but the actuality that you will be demography an absorption in their career development should crop assets in the end.
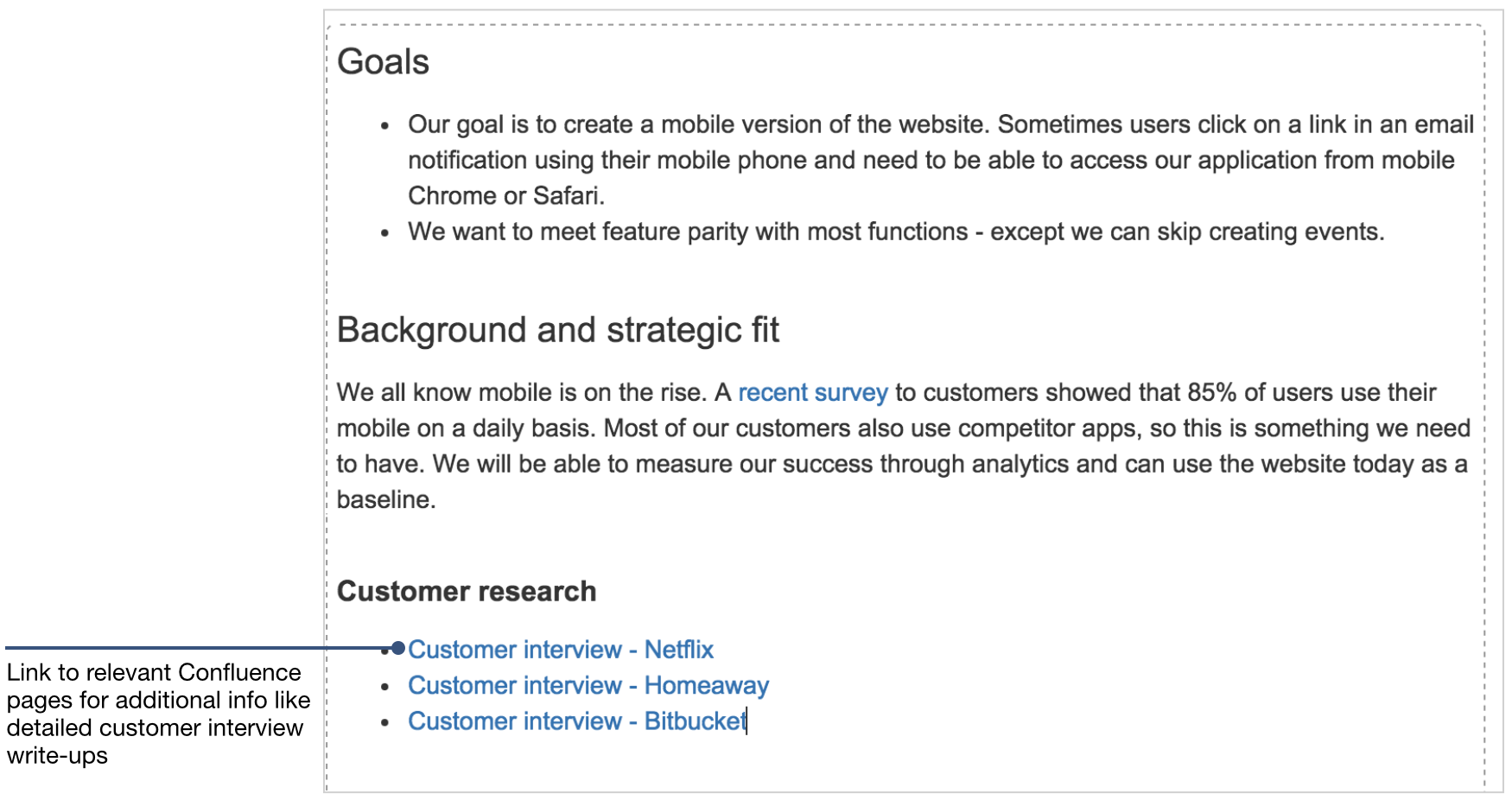
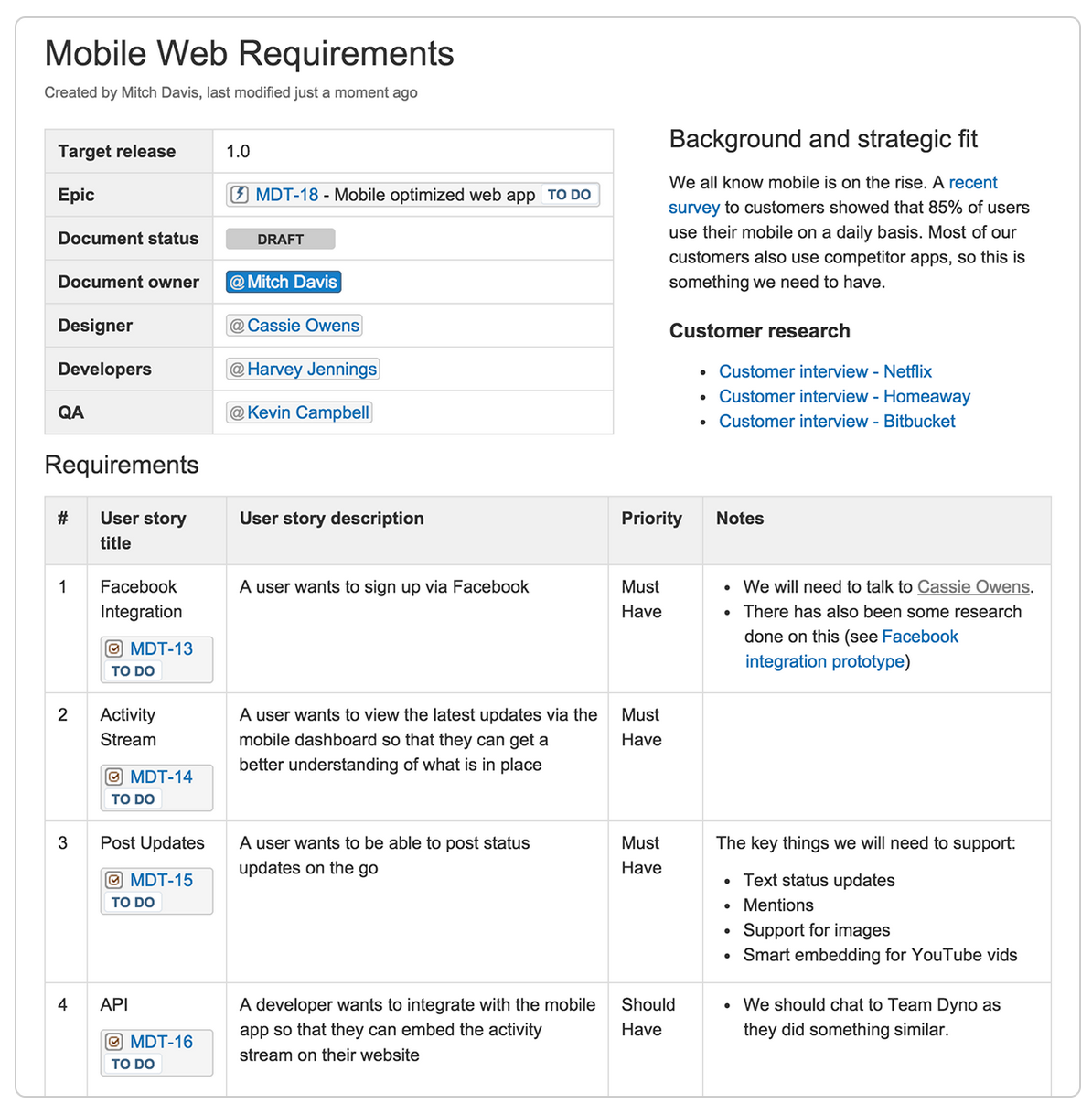
How To Write Requirements – How To Write Requirements
| Encouraged in order to my own weblog, in this particular occasion I am going to teach you about How To Delete Instagram Account. And from now on, here is the initial impression:

Why don’t you consider impression above? can be which remarkable???. if you feel consequently, I’l t explain to you a number of impression yet again down below:
So, if you wish to secure the fantastic pictures related to (How To Write Requirements), press save icon to download these photos to your pc. They are prepared for download, if you love and want to take it, just click save logo in the article, and it’ll be immediately downloaded to your computer.} Finally if you need to receive new and the recent picture related with (How To Write Requirements), please follow us on google plus or book mark this page, we attempt our best to give you regular update with all new and fresh pics. Hope you enjoy staying here. For most up-dates and latest information about (How To Write Requirements) pictures, please kindly follow us on twitter, path, Instagram and google plus, or you mark this page on bookmark area, We attempt to provide you with up-date periodically with all new and fresh images, enjoy your browsing, and find the perfect for you.
Thanks for visiting our website, contentabove (How To Write Requirements) published . Nowadays we are pleased to declare we have found a veryinteresting nicheto be discussed, namely (How To Write Requirements) Many individuals attempting to find info about(How To Write Requirements) and certainly one of them is you, is not it?