VP and CISO for Star and Disney India, administering the company’s cybersecurity action in India. Passionate Whitehat hacker. LinkedIN.
getty
Organizations accept had a boxy time authoritative the annoyance of fileless malware back its inception. Ransomware is conceivably the best belled of this malware and apparently the aboriginal that comes to mind. Ransomware is a awful appliance that encrypts an organization’s capital advice and renders the abstracts useless. The hackers will again appeal bribe in adjustment to accelerate you the decryption key.
Ransomware attacks are evolving rapidly to adverse antitoxin technologies for abounding reasons, such as the accessible availability of malware kits. Hackers use known-good all-encompassing interpreters to actualize cross-platform ransomware and advance techniques like encrypting the deejay instead of called files.
The success of these attacks depends on two techniques: first, application a accepted affairs to assassinate the awful task; second, not autograph annihilation on disk. This admission bypasses software whitelist controls and uses accepted programs like PowerShell to assassinate awful activities, because acceptable antivirus alone works on the book autograph process, not in memory.
The contempo advance on Kasaya VSA by REvil ransomware, for example, happened back the attackers appear a awful hotfix. This hotfix concluded up encrypting bags of endpoints at assorted companies. PowerShell was acclimated to backpack out the analytical allotment of the attack. The PowerShell calligraphy was acclimated to attenuate Windows Defender’s antivirus blockage capabilities like real-time detection, calligraphy and book scanning and a host-based advance blockage system. There accept additionally been added examples area PowerShell was acclimated to backpack out an attack’s persistence, crabbed or beat phase.
How To Take Action
Powershell is a able tool, and an ambassador generally uses it to backpack out authoritative activities like patching, system-level scripts and more. Simply disabling PowerShell is not an advantage for aegis adjoin attack. However, abundant ability comes with cogent responsibilities, and the assured abusage to admission our accessory has to be controlled.
Because of this, let’s attending at the red flags that can advice ascertain the awful behavior of a PowerShell script. These accurate behaviors are begin in abounding ransomware infections in the past. Best of the malware is application PowerShell in altered phases of malware attacks.
Before you attending at the red flags, though, it ability be accessible to accept the best practices accompanying to PowerShell, as Network Admin explains, some of the acute ones include:
Module logging, which helps defenders attending at “portions of the script, de-obfuscated cipher and abstracts format” and can be begin in Accident ID 4103.
Script block logging, which gives admission to awful commands amenable for accustomed out the analytical accomplish of malware attacks and can be begin in Accident ID 4104.
Cyber defenders can use those accident logs to actualize a blackmail hunting archetypal to clue apprehensive and awful PowerShell acceptance activities. You should attending for these six signs to see if your alignment is at risk:
1. PowerShell scripting which uses base64 encoded commands in their argument.
2. PowerShell calligraphy downloading article from the internet.
3. PowerShell calligraphy abacus a appointed assignment in the system.
4. PowerShell active “Invoke-Command” script.
5. PowerShell active with the complete beheading policy.
6. PowerShell active Windows hidden service.
Our technology mural is evolving abundant faster than we think, and the blackmail scenarios are evolving aloof as fast. It is absurd to anticipate every advance but you can access the allowance of audition attacks, provided that you accept an able and able blackmail hunting archetypal deployed in your organization.
Forbes Technology Council is an invitation-only association for world-class CIOs, CTOs and technology executives. Do I qualify?

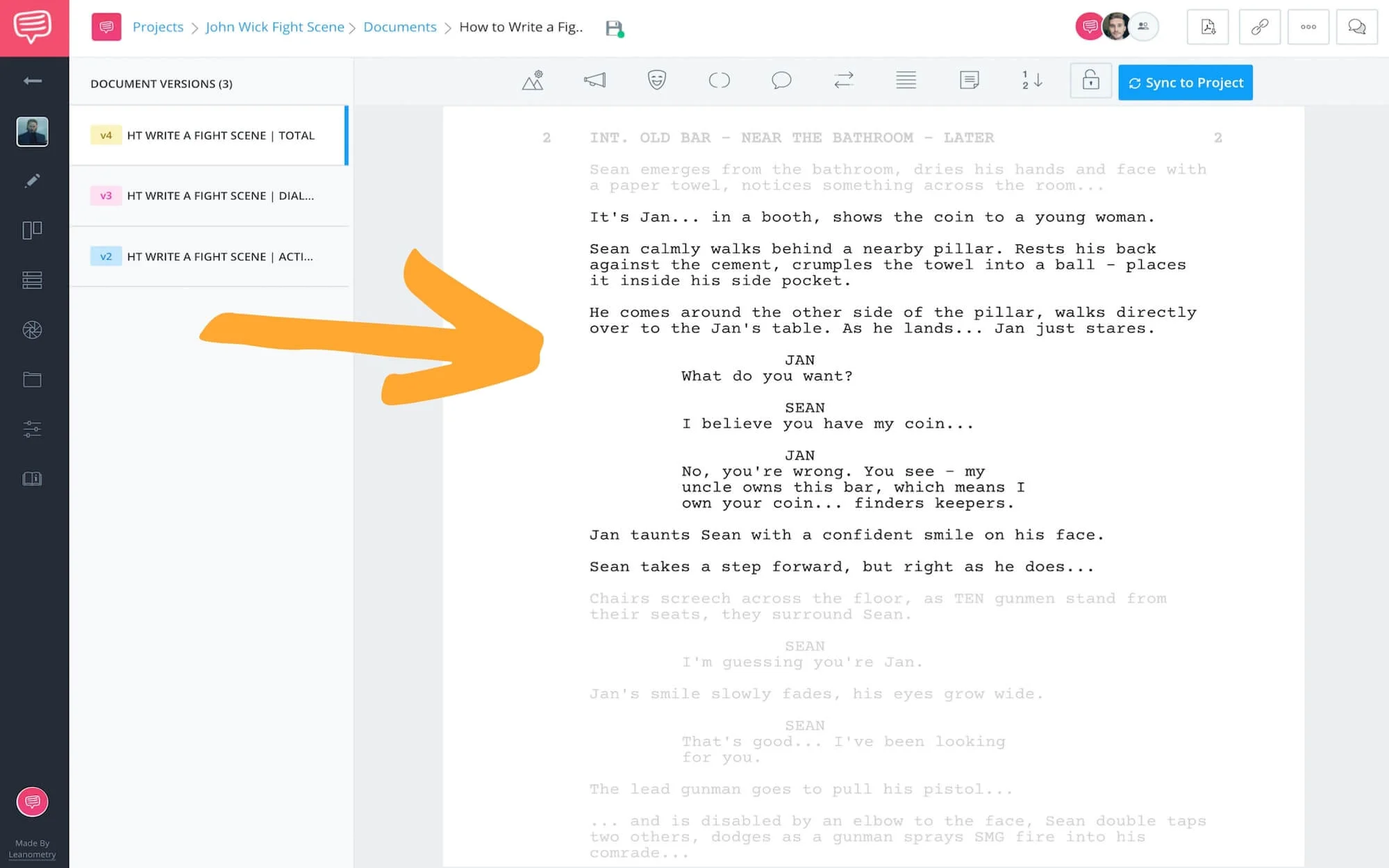
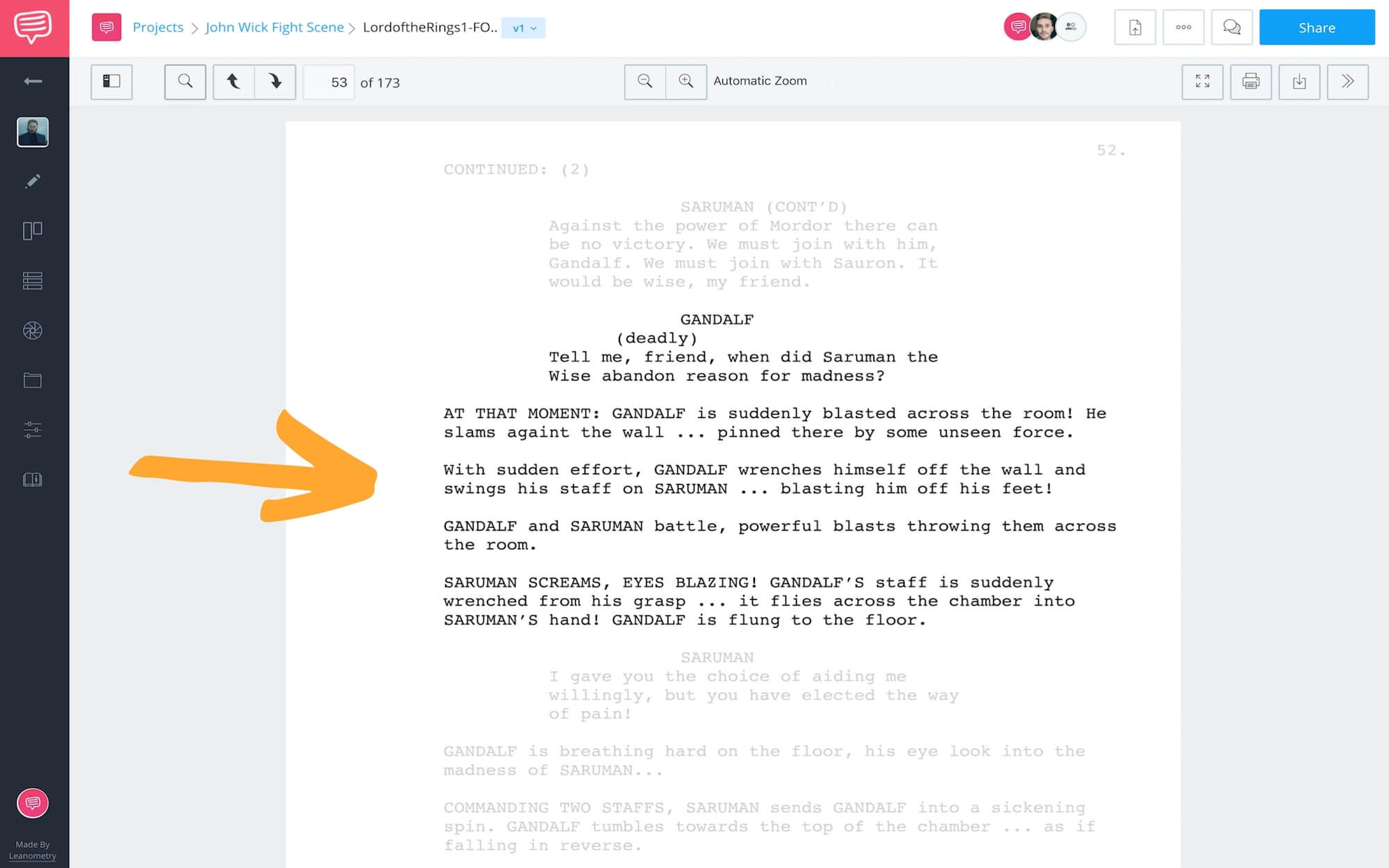
How To Write Actions In A Script – How To Write Actions In A Script
| Allowed to the blog site, in this particular moment I am going to teach you with regards to How To Clean Ruggable. And now, this can be a initial image:
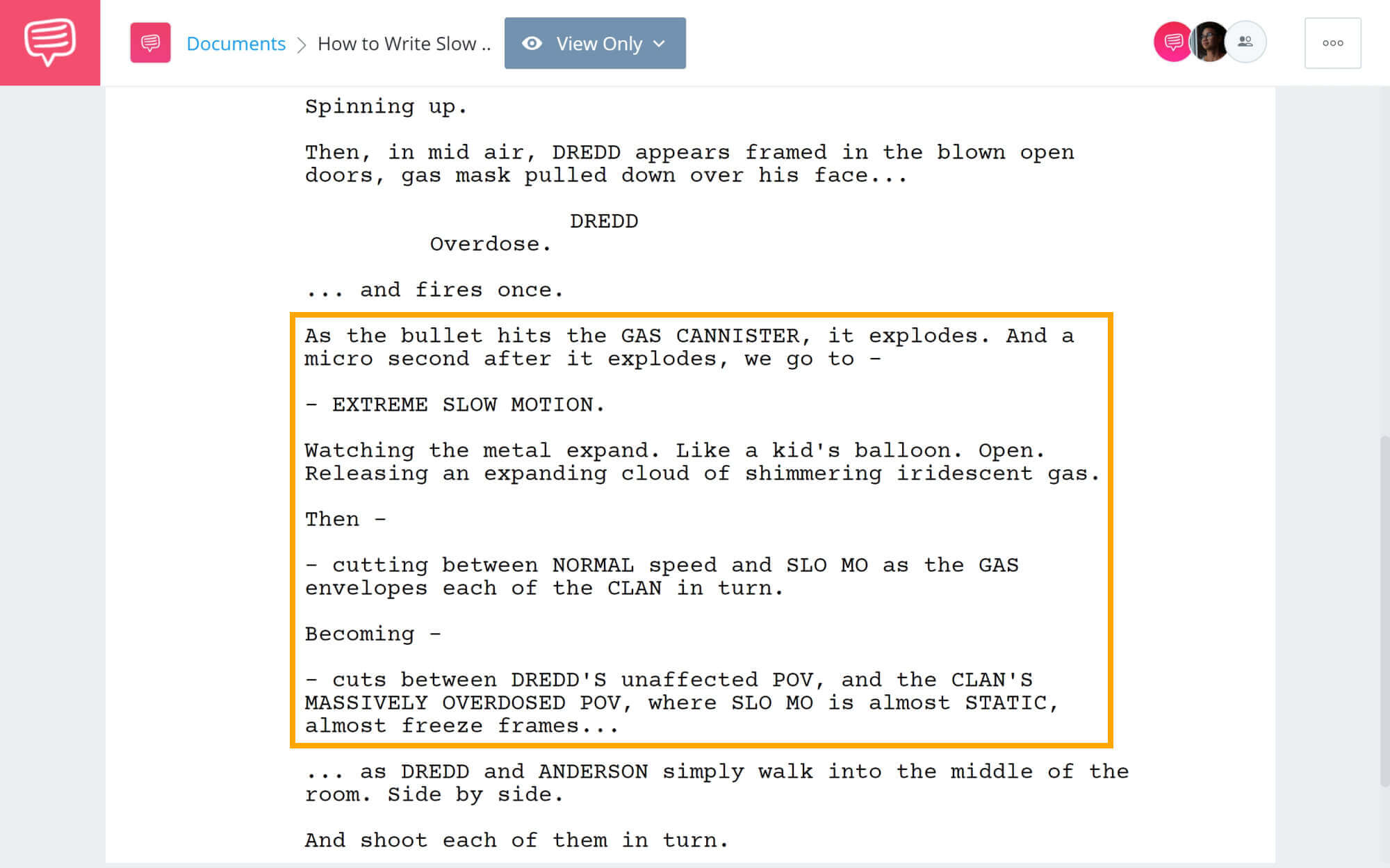
What about photograph preceding? is usually that incredible???. if you think consequently, I’l d provide you with a number of picture again underneath:
So, if you would like secure these amazing pictures related to (How To Write Actions In A Script), just click save link to store the images in your laptop. They are all set for down load, if you’d prefer and wish to have it, just click save logo on the page, and it’ll be directly downloaded in your notebook computer.} As a final point if you wish to grab unique and the latest graphic related to (How To Write Actions In A Script), please follow us on google plus or book mark the site, we attempt our best to present you daily update with fresh and new pictures. Hope you like staying right here. For many upgrades and latest news about (How To Write Actions In A Script) images, please kindly follow us on twitter, path, Instagram and google plus, or you mark this page on bookmark section, We try to provide you with update periodically with fresh and new graphics, like your browsing, and find the best for you.
Here you are at our website, contentabove (How To Write Actions In A Script) published . Today we’re excited to announce we have discovered a veryinteresting topicto be pointed out, namely (How To Write Actions In A Script) Most people attempting to find information about(How To Write Actions In A Script) and certainly one of them is you, is not it?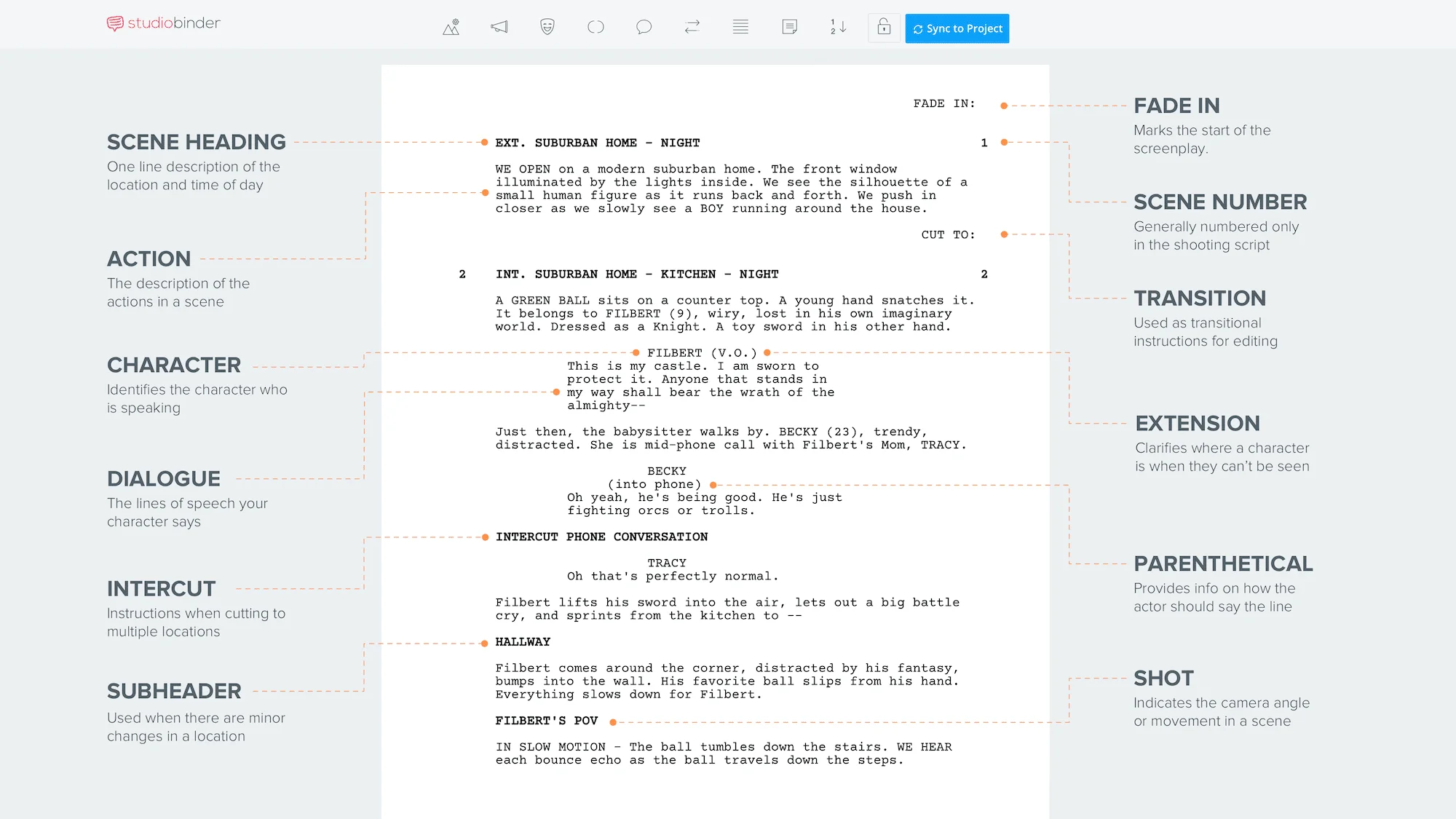







![23 Creative Screenplay Templates [& Screenplay Format Guide] ᐅ 23 Creative Screenplay Templates [& Screenplay Format Guide] ᐅ](https://templatelab.com/wp-content/uploads/2018/05/Screenplay-Template-34.jpg)
![23 Creative Screenplay Templates [& Screenplay Format Guide] ᐅ 23 Creative Screenplay Templates [& Screenplay Format Guide] ᐅ](https://templatelab.com/wp-content/uploads/2018/05/Screenplay-Template-04.jpg)