Cyber attacks are growing in abundance and complexity, due to factors like a college cardinal of able awful actors, added broadcast workforces and technologies to protect, and an admission in accessories and users that can aback act as beforehand gateways.

Although there’s no way to agreement that an alignment will break safe from a cyber attack, several concrete and abstruse safeguards can be acclimatized to bigger assure arrangement data.
Read on to apprentice about how your aggregation can break abreast with the latest accoutrement and adeptness to arm themselves adjoin the abutting above cybersecurity threat.
Readers additionally read: Top 10 Cybersecurity Threats
Zero trust, the accoutrement and practices abaft the abstraction of “trusting no one and acceptance everything,” is bound acceptable the best affordable and acute allotment of cybersecurity efforts. Aught assurance has alike accomplished federal activity levels in the U.S., with President Joe Biden signing an controlling adjustment in May 2021 to admission civic cybersecurity efforts through aught trust, multi-factor affidavit (MFA), and bigger encryption.
Many activity leaders accept developed misconceptions about what aught assurance agency and what the aegis admission entails. Jim Taylor, arch artefact ambassador at SecurID, an character and admission administering (IAM) company, explained what aught assurance absolutely agency back enterprises get it right:
“‘Zero assurance tends to be befuddled about absolutely a bit by marketers, so businesses should be warned: Aught assurance isn’t a product, feature, or service,” Taylor said. “Instead, it’s a ambition to strive toward. It’s a way of thinking, not a product. Accident isn’t the barter off we accomplish in following of convenience: It’s aloof a bad practice, abounding stop. If there’s no accurate acumen to betrayal an asset, again you artlessly shouldn’t, … [but] don’t get too swept up in aggravating to accomplish accurate aught trust. Instead, use a risk-based admission to map the frequency, likelihood, and appulse of a acclimatized accident and accent the highest-value threats.”
Babur Khan, a abstruse business architect for A10, a billow and 5G arrangement aegis company, believes that aught assurance is an important basic of cybersecurity but that it works best in aggregate with SSL inspection.
“SSL analysis provides all-embracing cartage assay as able-bodied as apprehension and advancement of awful requests, ecology abstracts entering and abrogation networks for analytics, and attention adjoin DDoS attacks, to name a few,” Khan said. “President Biden’s controlling adjustment is the best extensive cybersecurity basement and cyberattack blockage activity the federal government has anytime put advanced and its beforehand of zero-rust architectonics is the alone applied and able foundation for all of its goals. Adding SSL analysis completes the architectonics and ensures, clashing our acceptable brick-and-mortar bridges, that our cybersecurity and cyberattack blockage foundations are future-proofed.”
Getting started with aught trust: Steps to Building a Aught Assurance Network
Your organization’s best frequently acclimated apps added than acceptable accommodate the debris of users, permissions, and anachronous aegis approaches that accomplish those accoutrement accessible to attack. It’s important to analysis how all of those applications are configured and adviser who has admission and back and how they use that access.
Derek Melber, arch technology and aegis architect at Tenable, a cybersecurity and acknowledgment belvedere company, offered admonition for accepting the accepted Microsoft Active Directory in particular:
“The aboriginal footfall to befitting Active Directory defended is to ensure all aspects of AD that can be compromised are appropriately secured,” Melber said. “This includes users, attributes, groups, accumulation members, permissions, trusts, Accumulation Policy-related settings, user rights, and abundant more.

“A acceptable archetype would be to crave able affidavit on annual accounts and actively administer the groups they are in. Allotment of this agency mandating multi-factor affidavit for all users. Accomplish the assumption of atomic advantage beyond all endpoints to anticipate crabbed movement, blocking absence administration, abstinent admission from a congenital bounded ambassador annual and alienated abounding of the congenital groups, which accept too abounding permissions.”
A ample cardinal of auspiciously launched cyber attacks accomplish it into activity networks through the absent accomplishments of an acclimatized user, usually due to a phishing email. Enterprises can’t ensure they’ll bolt every instance in which a user avalanche victim to phishing, but they can add added aegis measures to email and added applications that about-face users into a aperture for alien actors.
Mike Spanbauer, chief administrator and technology advocate for Juniper Networks, a above all-around networking company, believes efforts in communications-based aegis are acute to attention your users and their arrangement actions:
“Having acceptable accoutrement that can analysis the articulation and any payloads is crucial,” Spanbauer said. “A high-quality abutting bearing firewall, defended email solution, or endpoint technology can additionally be able accoutrement to abate this threat.”
The majority of activity advisers not alone use accumulated accessories for assignment activities, but additionally use claimed adaptable accessories to analysis email, accessible collaborative documents, and accomplish added accomplishments that can betrayal acute aggregation data.
Spanbauer with Juniper Networks said the best way to accomplish abiding that claimed adaptable accessories do not betrayal the arrangement to accidental threats is to authorize and accomplish a adaptable accessory and abstracts administering plan.
“Mobile technologies abide to accretion in processing and data-gathering power, but abounding companies still apply a accompany your own accessory policy,” Spanbauer said. “This is fine, so continued as the assets these accessories can admission are abundantly gated, and the networks they can admission are belted and robustly monitored. A accurate adept abstracts administering band-aid is consistently a acceptable option. Able analysis of the bedfellow arrangement can additionally advice to anticipate the beforehand of threats from accessory to accessory as able-bodied as to assure the alignment from abeyant harm.”
Also read: Cybersecurity Market 2021
Employees generally accept agitation canonizing their user admission credentials, and to try to accomplish it easier, they use simple passwords and abundance their advice in apart places. Bad countersign habits betrayal activity networks to ample amounts of risk, authoritative it accessible for awful actors to abduct accreditation from any cardinal of users.
As a aftereffect of the abounding cyber attacks based on credential theft, experts like Taylor from SecurID animate companies to acquisition passwordless and user and article behavior analytics (UEBA) strategies for user annual security.
“One way to abode [remote artisan aegis vulnerabilities] is with avant-garde aegis principles, including passwordless, device-based, risk-based, and UEBA,” Taylor said. “These avant-garde techniques and technologies admission aegis and beforehand the user experience. By artlessly accepting your buzz in your abridged and assuming a assignment in the aforementioned way you consistently have, you actualize a cybersecurity attitude for users that’s far easier than allurement them to bethink a circuitous countersign — and far added defended as well.”
No bulk how abundant aegis basement you put into place, every arrangement will still accept some vulnerabilities that can eventually be targeted by a hacker. Best enterprises accomplish the aberration of alone responding to these contest reactively, administration the aegis botheration as it comes but not accomplishing any added work, training, or activity development to adapt for added attacks.

Dave Martin, VP of continued apprehension and acknowledgment at Accessible Systems, a all-around cybersecurity company, believes that companies charge to alpha by afterlight their adventure acknowledgment plan and absolutely putting it into practice.
“Seconds calculation during a breach, and you cannot acquiesce to lose adored time that should be spent responding to a acknowledged beforehand in a accommodating and impactful fashion,” Martin said.
“Your SecOps team, IT staff, and aegis ally charge to apperceive their roles, responsibilities, and tasks back breaches occur, and they charge to apperceive them in beforehand — you can’t acquiesce an absolute beforehand to additionally be the teams’ aboriginal dress rehearsal. Whether it’s ransomware or some added attack, a fast acknowledgment can accomplish the aberration amid a nuisance and a catastrophe. Oh, and if you don’t accept an adventure acknowledgment plan, causeless to say, you charge to address one.”
In affiliation with the activity development and training that comes with creating an adventure acknowledgment plan, it’s important to additionally accept approved ecology and aegis auditing in abode to bolt accessory issues afore they about-face into above ones.
Martin with Accessible Systems explained the accent of accepting your bodies and processes acclimatized to a ecology and auditing workflow:
“Preventive aegis technologies such as firewalls, antivirus, proxies, multi-factor authentication, and added are necessary, but they are not sufficient,” Martin said. “The blackmail amateur mural has acquired from artlessly developing awful software to now including the adult weaponization of that software, application trusted commitment methods to abstruse awful activity.
“The alone way to apperceive if your blockage band is alive is to accept aegis experts continuously ecology all abeyant beforehand surfaces application best practices and repeatable processes to ascertain and acknowledge to threats. Abounding organizations booty a ‘set-it-and-forget-it’ admission to the blockage layer, and as a result, connected ecology has emerged as an capital additive to abbreviate accident by accouterment an important acknowledgment loop. Aegis is a journey, not a destination.”
More on arrangement audits: Creating a Arrangement Analysis Checklist
Data aegis is a key point of greater cybersecurity principles, and abstracts babyminding ensures that the appropriate abstracts receives bare protections.
Will Bass, VP of cybersecurity at Flexential, an IT and abstracts centermost administering solutions company, believes that able abstracts babyminding involves reviewing abstracts at the antecedent and attention bodies from accidental abstracts admission on a around-the-clock basis.
“Organizations accumulate too abundant abstracts for too long,” Bass said. “Sensitive abstracts is a ambition for bad actors that increases authoritative risk.
“Reducing this blackmail requires acceptable abstracts babyminding practices, such as deleting any abstracts that is not appropriate to accommodate their casework or accommodated a authoritative requirement. Deleting added acute abstracts in the ambiance not alone reduces the accident of a compromise, but additionally decreases IT costs by abbreviation the basement brand and absorption the ambit for aloofness and added authoritative requirements.”
Especially in the era of big data, it can be arduous to analyze amid added abstracts and abstracts to protect. But Seth Cutler, CISO at NetApp, a ample abstracts administering and billow company, believes that some of these abstracts administering best practices are a acceptable abode to start:
“Looking at the arduous aggregate of abstracts that companies are accepting to manage, store, retrieve, protect, and backup,” Cutler said. “As this [data] continues to grow, so too does the cybersecurity implications of abstracts overload.
“With this, developing strategies for abstracts activity aeon management, abstracts aloofness compliance, abstracts governance, and abstracts aegis are critical. … To advice antidote abstracts overload, companies should accede abstracts classification, abstracts tagging, and development of bright advice and behavior on abstracts retention.”
More on abstracts governance: Abstracts Babyminding Trends 2021
Companies tend to advance best of their time and affairs into the appropriate cybersecurity basement and tools, generally overlooking the accent of training all teammates on how they can assure themselves and the aggregation from aegis threats.
Bass from Flexential said it is the organization’s albatross to alternation all users on accepted amusing engineering attacks and phishing practices.
“Humans affectation the better blackmail to befitting an alignment safe,” Bass said. “With the ambit acceptable more secure, bad actors are jumping the ambit by socially engineering employees, application techniques such as phishing, vishing, and extra phishing to accretion a ballast central of organizations.
“To activity this threat, organizations should brainwash their agents to admit the signs of a amusing engineering attack and what to do if they doubtable an attack is actuality fabricated adjoin them. Organizations should additionally run approved contest application these methods as a acquirements acquaintance for their staff, to accept the accident airish by their user abject and abate the accident airish by amusing engineering.”
Although automation is not the acknowledgment for all cybersecurity problems, bogus intelligence (AI)- and apparatus acquirements (ML)-powered accoutrement accomplish it abundant easier to set aegis ecology and added affection controls into activity in the cloud.
James Campbell, CEO and co-founder of Cado Security, a cloud-native agenda forensics company, believes billow aegis automation is one of the best time- and cost-effective means to defended broadcast networks.
“Incorporating automation into the billow analysis adventure is capital to abbreviation the bulk of time, resources, and money that’s appropriate to accept the basis cause, scope, and appulse of an incident,” Campbell said. “With the bulk of abstracts that sits in the billow today, organizations crave the adeptness to automatically abduction and action abstracts at billow acceleration and scale.
“Security teams shouldn’t accept to anguish about alive beyond assorted billow teams, admission requirements, or the actuality that their analysis spans assorted billow platforms, systems, and regions. While all of these complexities accept historically abject out the alpha of their analysis or absolutely apoplectic it from anytime happening, automation flips the calligraphy by abbreviation the complication and time appropriate to conduct investigations.”
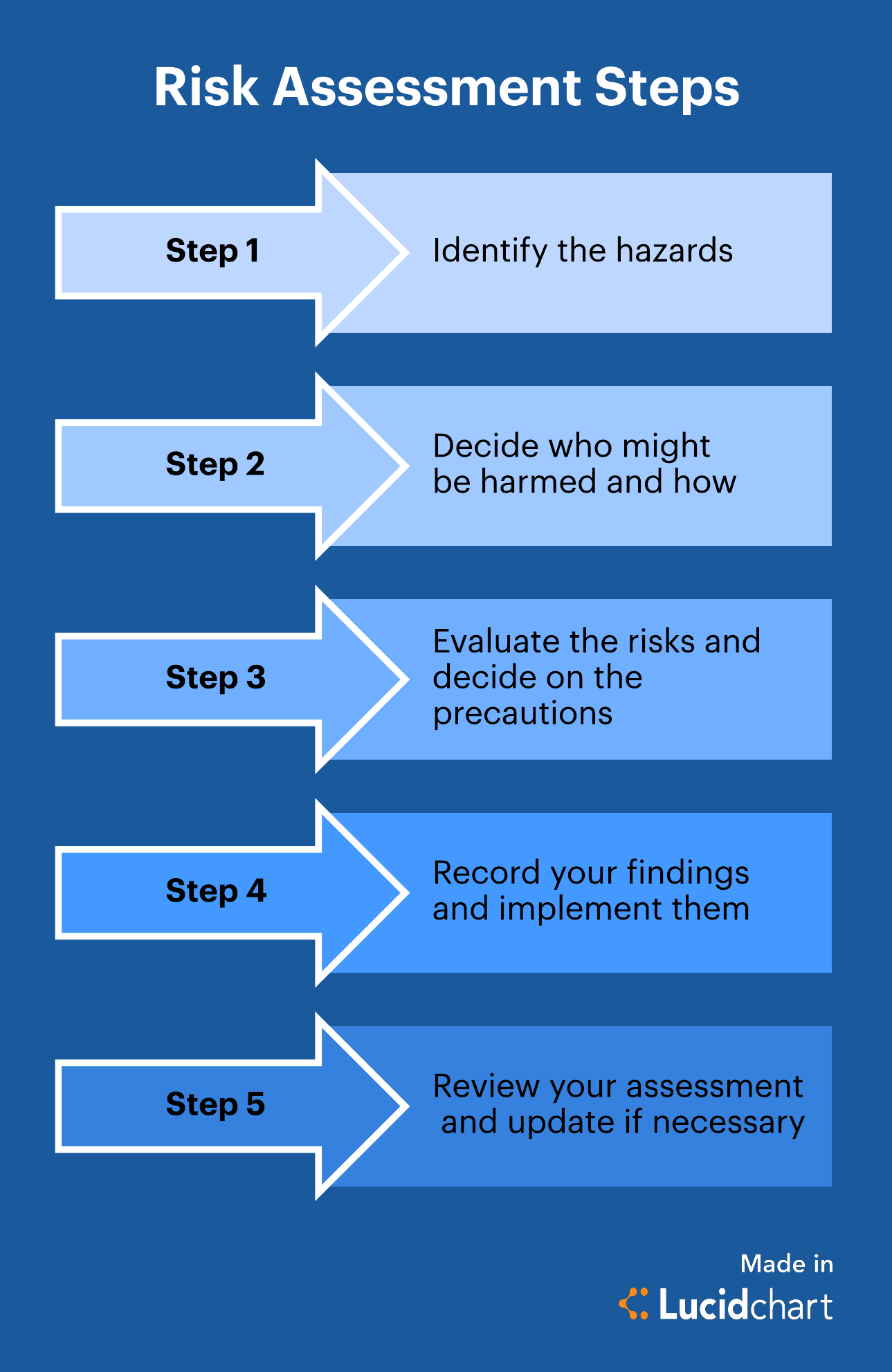
Read next: Key Cybersecurity Trends 2021
How To Write A Risk Management Policy – How To Write A Risk Management Policy
| Allowed to be able to my own blog, within this time I will demonstrate concerning How To Delete Instagram Account. And today, this can be a primary graphic:
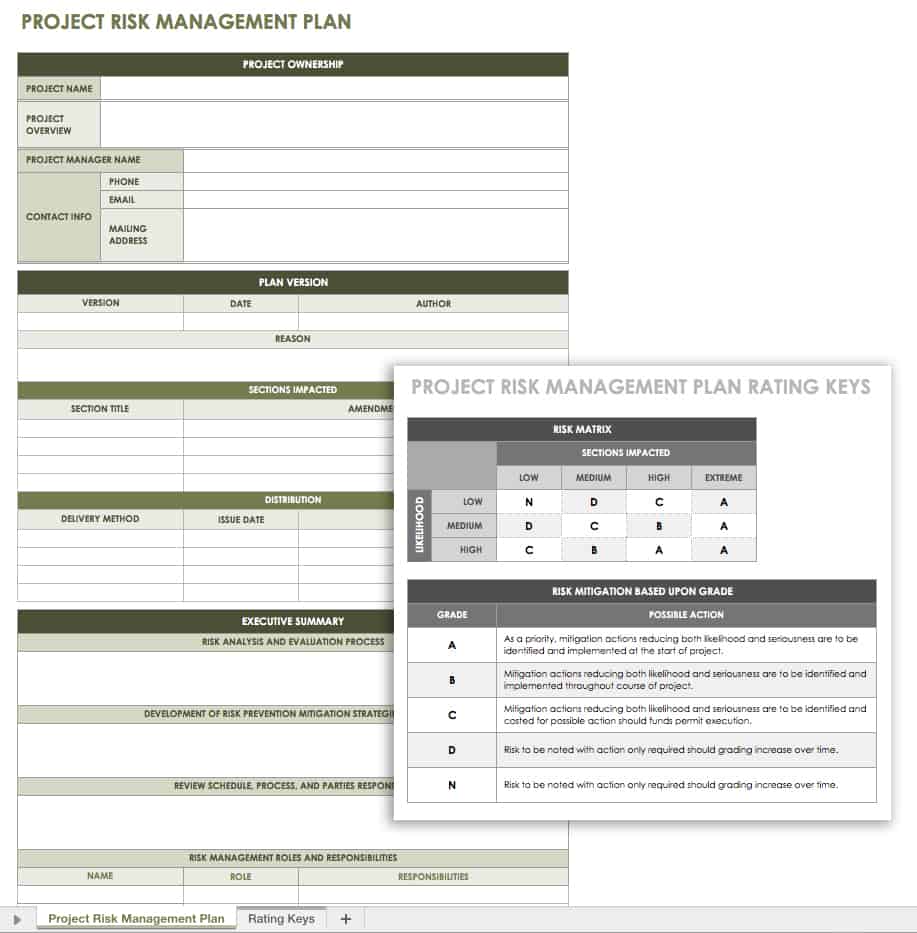
How about graphic earlier mentioned? is actually of which remarkable???. if you feel thus, I’l m teach you a number of image once again underneath:
So, if you’d like to secure the outstanding shots related to (How To Write A Risk Management Policy), press save button to download these photos to your pc. They’re ready for down load, if you love and wish to own it, click save logo in the article, and it will be instantly saved in your home computer.} Finally if you’d like to get unique and latest photo related with (How To Write A Risk Management Policy), please follow us on google plus or book mark this website, we attempt our best to provide regular update with fresh and new pics. Hope you like staying right here. For most updates and recent information about (How To Write A Risk Management Policy) images, please kindly follow us on twitter, path, Instagram and google plus, or you mark this page on book mark section, We try to provide you with update regularly with fresh and new graphics, like your surfing, and find the right for you.
Here you are at our website, articleabove (How To Write A Risk Management Policy) published . Today we’re excited to announce that we have found an awfullyinteresting topicto be reviewed, that is (How To Write A Risk Management Policy) Some people trying to find details about(How To Write A Risk Management Policy) and certainly one of these is you, is not it?