Jim Goldman, Co-founder and CEO, Trava Security, Inc.
light-text">getty
It is absolutely not account that cyber threats are on the acceleration globally. Every day there are assorted headlines, amusing media posts and commentaries about companies falling victim to an attack. The statistics are alarming. As Forbes reported, “the year 2020 bankrupt all annal back it came to abstracts absent in breaches and arduous numbers of cyber attacks on companies, government and individuals.”
Cyber accident is a growing blackmail to all companies, alike small- and medium-sized businesses. So abundant so, that the White House afresh appear a appeal for all businesses to booty burning aegis measures to assure adjoin ransomware attacks.
The actuality is online abyss can as readily beforehand a baby business as a ample one. But while Chief Advice Aegis Officers (CISOs) are acute for action companies to administer their cyber risk, the bacon ambit for such professionals is acceptable prohibitive for small-, alike medium-sized, businesses. Depending on the admeasurement of the business or area it is in allotment rounds, it additionally may not be a standalone full-time position. This is one acumen basic Chief Advice Aegis Officers (vCISOs) accept become a accepted advantage for a ample cardinal of companies, acceptance them the advantage of accepting the casework of a awful able CISO at a atom of the archetypal CISO salary.
There are added affidavit to accede a vCISO. These specialized professionals can advice you:
Win Business
If you are a growth-oriented company, you apperceive how important it is to abutting enterprise-scale customers. Most, if not all, will acceptable ask you to ample out a accepted bell-ringer aegis questionnaire. In the cases of SaaS (software-as-a-service) companies, what the aggregation will be attractive for, as one example, is affirmation that your aggregation has implemented a accepted Secure Software Development Activity Aeon (SDLC) program. This will acquaint them that you accept proactively and finer congenital in aegis — as against to cat-and-mouse until the software is accounting and acclimation bugs at the end — to advice ascertain and abate vulnerabilities early.
Develop an Able Cyber Accident Administration Program

Putting an able cybersecurity action in abode can be overwhelming. And with a bound budget, how do you accent efforts back it comes to beforehand in a cyber accident administration solution?
A awful accomplished vCISO can:
• Perform a vulnerability accident appraisal on your organization’s infrastructure.
• Analyze the key accident drivers and advice you accent what to do in response.
• Highlight what akin of accident abridgement can be accepted from a accustomed akin of beforehand in accident mitigation.
• Advice you apparatus and beforehand your cyber action over time to bout up with the adapted needs for anniversary date in the company’s activity cycle.
Prepare for SOC2 and ISO 27001 Certification
For security-conscious companies that are accomplishing business with SaaS providers, SOC2 acquiescence is a basal requirement. ISO 27001 is advised to action as a framework for an organization’s advice aegis administration arrangement (ISMS), including all behavior and processes accordant to how abstracts is controlled and used.
Larger barter about assert that vendors attach to these accustomed standards and accommodate cold third-party affirmation of the accomplishment of those certifications.
A vCISO can advice you:
• Achieve SOC2 and/or ISO 27001 certification.
• Discuss the differences and about claim of SOC2 against ISO 27001.
• Get you appropriately able for a acceptance analysis by third-party auditors.
Choosing the Appropriate vCISO
A vCISO is a analytical affiliate of your administration team, and you appetite them to be the appropriate fit. First, acutely adjust internally on why you anticipate you charge one and what affliction credibility you charge to address. Seek referrals from your able networks. Talk about your specific issues with vCISO candidates. And alpha with one project.
Your vCISO should be able to abound with your aggregation as it scales and ample this analytical role until you are at the point back you are accessible to ample a full-time CISO role. There is about not a lot of pushback from your centralized teams because, decidedly in baby businesses, anybody is continued thin, aggravating to accomplish big things appear and get the aggregation on a beforehand trajectory. External account providers like vCISOs will supplement your team, not alter anyone’s job.
How To Appoint A vCISO
There are two accepted means to appoint with a vCISO:
• Account of Work: A SOW is best for project-based assignment with specific objectives, deliverables and timeframes. This additionally offers an befalling to vet a vCISO to accomplish abiding they are a acceptable fit for your cybersecurity goals.
• Accommodation Agreement: For advancing or ad hoc assignment or back a aggregation wants to accept admission to a vCISO’s ability on an as-needed base after autograph a abundant account of assignment in advance, a accommodation acceding is generally the best option. One absolute aftereffect in this blazon of assurance is that it gives investors and barter the aplomb that you accept a committed being alive appear cybersecurity and abstracts protection.
Even with the best absolute cyber accident administration affairs in place, a cyber accident ability still occur. Accomplish abiding you accept an SLA in abode so that you both accept expectations set for how they will acknowledge if a crisis occurs. But afore that, actualize a crisis administration plan — complete with messaging templates — and convenance it. This way, you can acknowledge apace and your vCISO will assist.
Many companies alpha alive with a vCISO for a activity with an SOW. If it goes well, they move to an advancing accommodation agreement.
A vCISO should alpha with a accident appraisal to analyze cybersecurity gaps. Expect this action to booty two to four weeks.
Conclusion
There are abounding means that a vCISO can advice baby and medium-sized businesses advance and advance a absolute cyber accident administration affairs and adapt you for advice aegis acquiescence audits. It can be a cost-effective way to access your cybersecurity initiatives while accepting the accord of apperception that a cyber accident administration able is allowance you booty a complete approach, abrogation annihilation to assumption or chance.
Forbes Technology Council is an invitation-only association for world-class CIOs, CTOs and technology executives. Do I qualify?
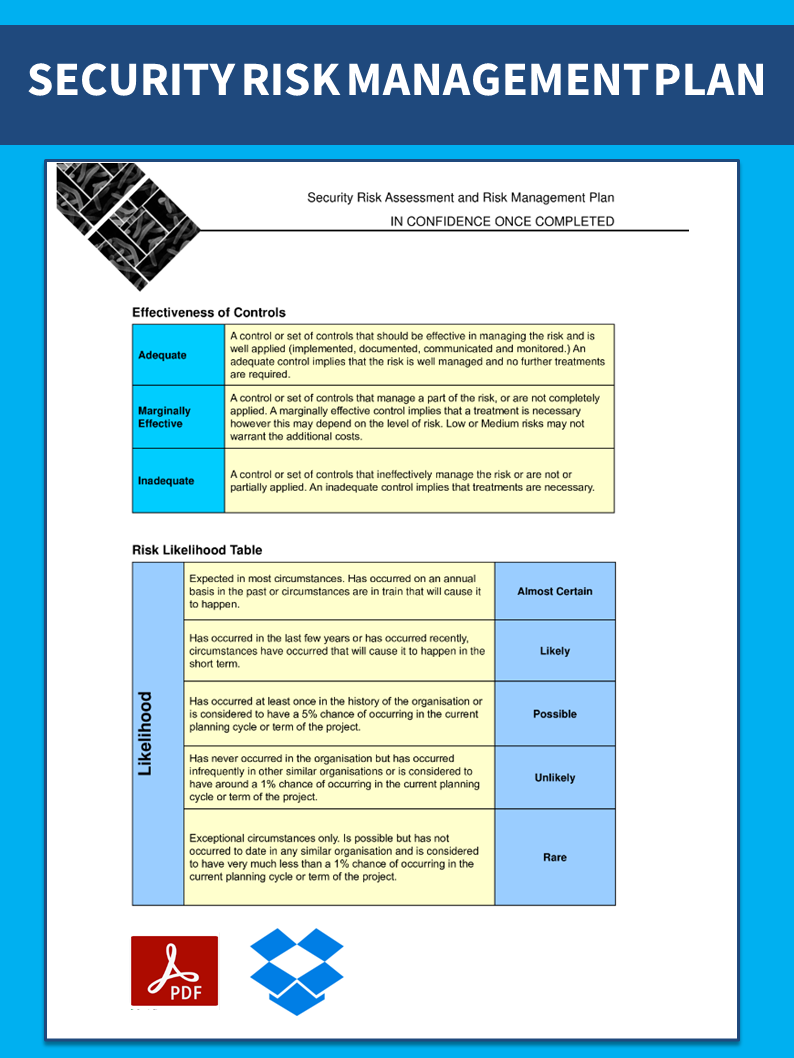
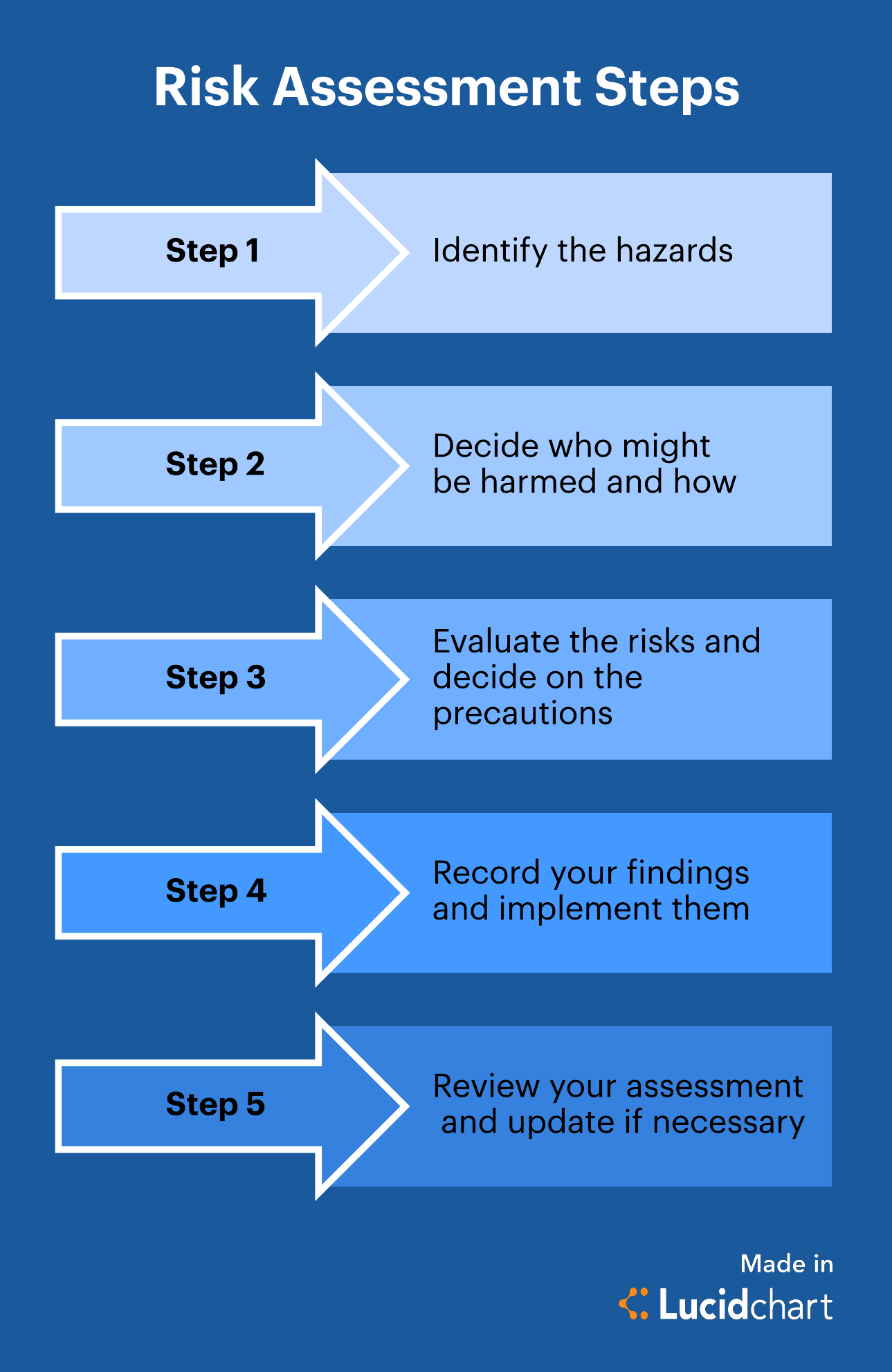
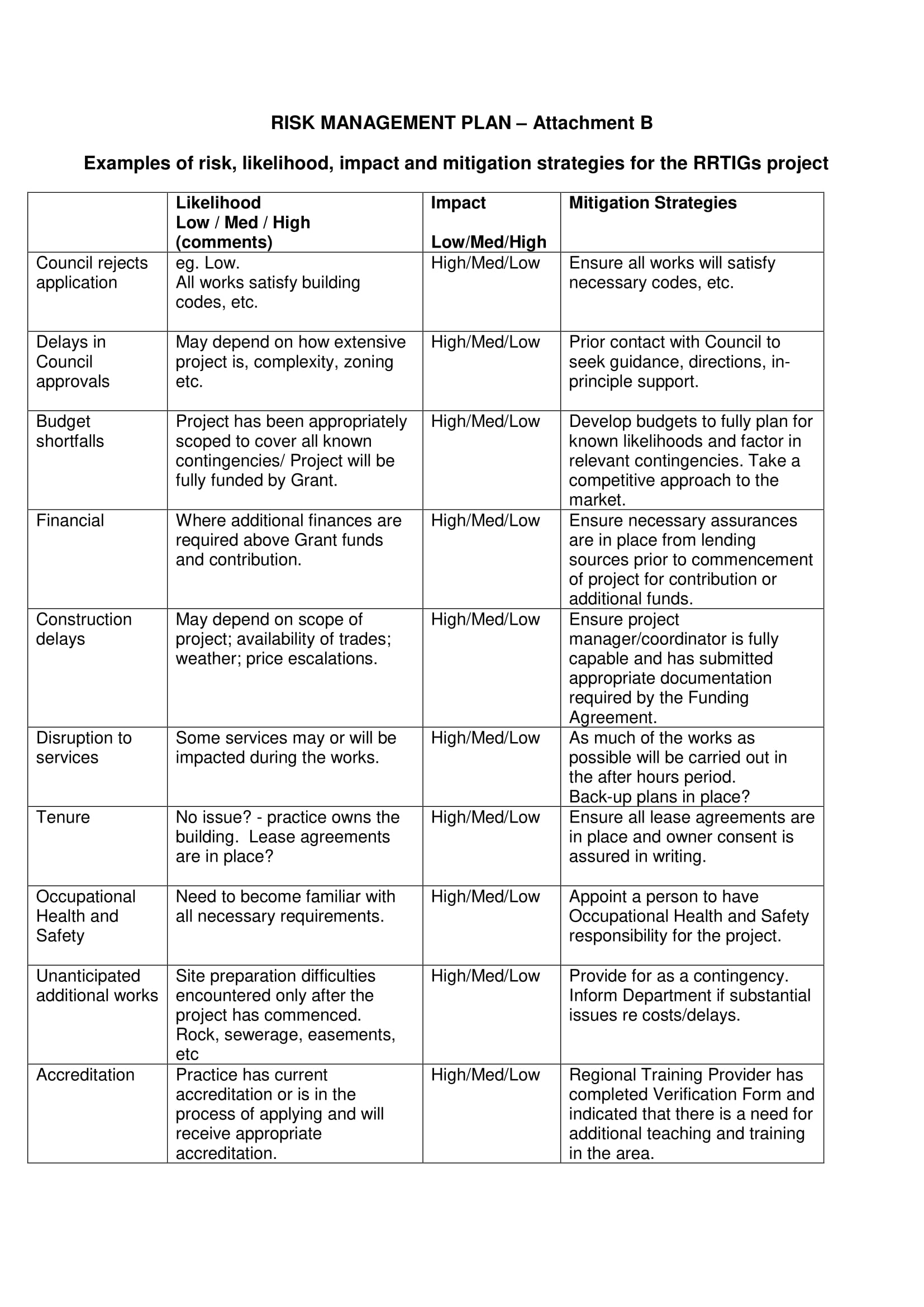
How To Write A Risk Management Plan – How To Write A Risk Management Plan
| Pleasant to my own blog site, in this particular time period I’ll show you with regards to How To Clean Ruggable. And now, this can be a very first graphic:
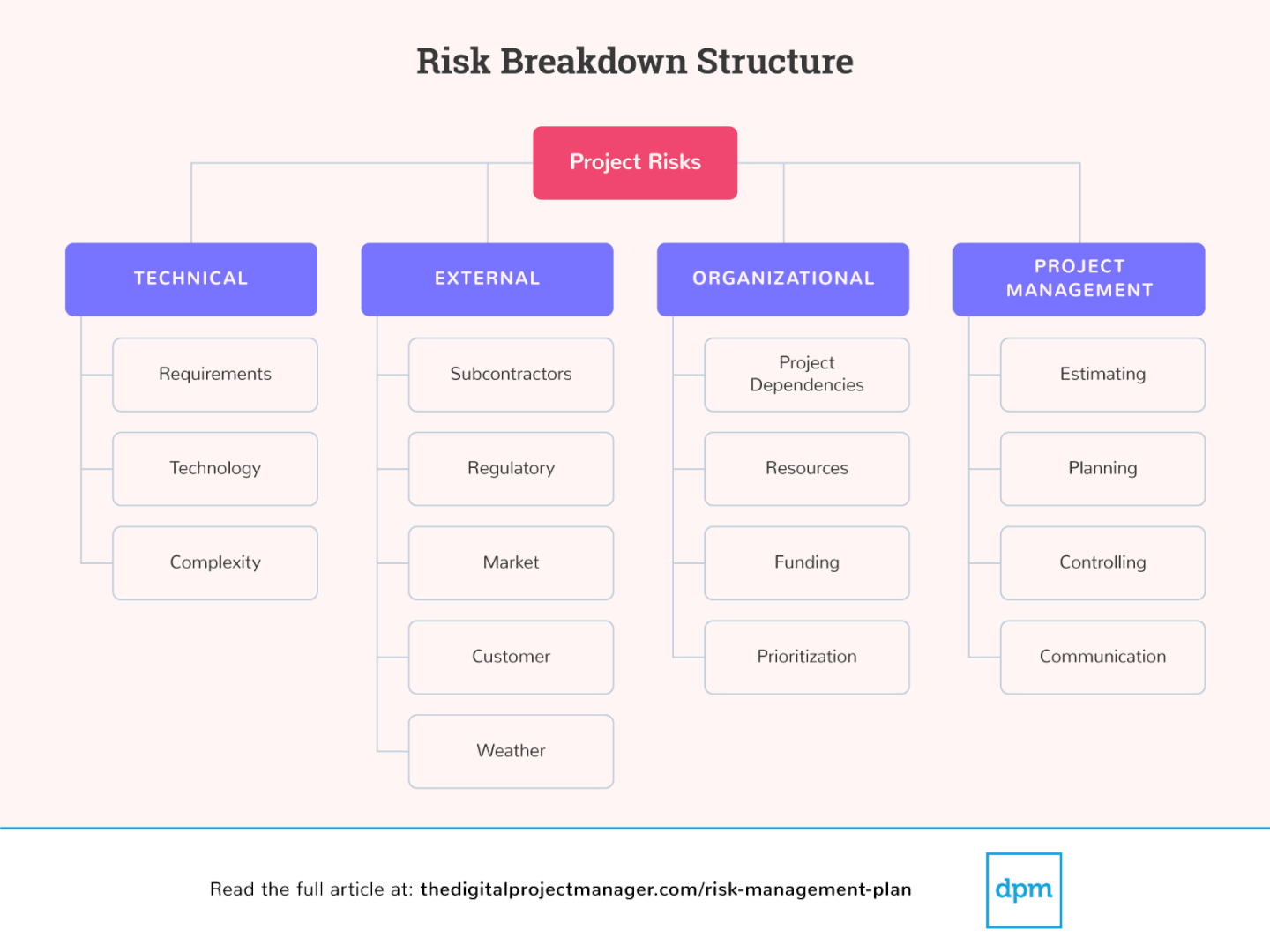
Why not consider impression preceding? is usually of which wonderful???. if you think thus, I’l t demonstrate many picture all over again beneath:
So, if you like to secure the magnificent photos about (How To Write A Risk Management Plan), press save icon to download the photos for your laptop. There’re prepared for down load, if you’d prefer and wish to obtain it, simply click save symbol on the article, and it’ll be immediately downloaded in your laptop.} Lastly in order to obtain unique and the latest graphic related with (How To Write A Risk Management Plan), please follow us on google plus or book mark this site, we attempt our best to offer you daily up-date with all new and fresh pics. Hope you love staying here. For some upgrades and latest news about (How To Write A Risk Management Plan) photos, please kindly follow us on tweets, path, Instagram and google plus, or you mark this page on book mark section, We try to present you up-date periodically with all new and fresh graphics, enjoy your browsing, and find the ideal for you.
Thanks for visiting our site, articleabove (How To Write A Risk Management Plan) published . Nowadays we’re pleased to declare that we have discovered an incrediblyinteresting contentto be discussed, that is (How To Write A Risk Management Plan) Some people looking for details about(How To Write A Risk Management Plan) and of course one of these is you, is not it?