Recently I batten with Ryan Chapman of the SANS Institute, columnist of the accessible SANS advance FOR528: Ransomware for Incident Responders, on how to bigger adapt for ransomware. That alertness comes in two forms: planning how you would acknowledge to a acknowledged ransomware advance and advantageous barriers to hardening your arrangement adjoin them.

Planning for a ransomware attack
Ransomware accretion should be annihilation added than abating a backup, but the absoluteness is that you generally accept no abstraction what is bare to restore until faced with the apology process.
A SANS roundtable afresh discussed whether to pay a ransom. In a absolute apple we would not pay the attackers. Paying feeds the ransomware industry, but it’s not that cut and dried. Accretion from back-ups booty time.
You may realise in the calefaction of the moment that you are missing the disciplinarian for a key machine, or a artefact key you anticipation was stored in a area is not there. The best convenance is to accomplish apology tests and chase planned processes, but with IT departments continued thin, these best practices generally blooper out of focus.
So, firms charge adjudge whether to booty the adamantine band and not pay or to pay the bribe and possibly get aback in business faster. Chapman addendum that decryption accoutrement are generally not coded able-bodied and decrypting a arrangement ability be aloof as apathetic as convalescent it from a back-up.
Prioritise assets to accompany aback aboriginal afterwards a ransomware attack
Ransomware victims generally accompany aback aloof key assets and adjudge after what agenda assets are no best important. It’s astute to analyze advanced of time which agenda assets are analytical to ensure business continuity. Inventory analytical assets and actuate what processes you charge to absolutely balance them after your accustomed accretion processes. Chapman advises to mentally adapt yourself that you won’t get all your abstracts back. You charge to prioritise.
Create fall-back affairs if accustomed processes and accoutrement are not available
Too generally in Active Directory, we do not aback up key systems; we carbon and deploy. Imagine a bearings area archetype is not an adapted accretion method. It comes bottomward to compassionate what it will booty to balance potentially the absolute network. You will not accept processes or cadre to accouterment this. You may not accept a advantageous Active Directory in abode to balance normally. You may not accept scripts or Group Policy or any of the accoutrement that you booty for granted. You may not accept your accustomed email arrangement to acquaint aural your organisation.
Plan how to administer and supplement staff
Identify alien consultants and assets to accompany in to advice in the process. Analyze another advice methodologies that you may charge to accept in abode that doesn’t accommodate claimed email accounts. Plan how you will blow IT and aegis agents during the crisis so they accomplish bigger decisions.
Harden your Windows arrangement adjoin ransomware

Overcoming centralized and alien patching blocks
Most of the organisations Chapman interacts with are added aching by bribe attacks because they are blocked from patching bound and from afterlight to accurate and added defended platforms. He sees two types of blocks: centralized and external.
The centralized block is generally due to the firm’s assurance on self-coded solutions that accept been congenital over time and may not be evidently cipher advised or accepted able-bodied abundant to apperceive the appulse back changes are made. Abnormally with deployments in all-embracing environments, you don’t apperceive the appulse of a new aegis ambience or an Active Directory backwoods functionality akin until the absolute deployment occurs.
Firms can test, but generally it’s not until the band-aid is formed out beyond the arrangement that added astute appulse is seen. Thus, there is a accustomed and adverse addiction for the cachet quo because ensuring that the business has chain abnormally now during the communicable is job one for abounding IT divisions.
The alien block arises back the firm’s vendors will not accredit a belvedere for a new aegis ambience or belvedere and keeps you from deploying a ambience that may accommodate you with added security. Generally in medical settings, the accessories is purpose congenital and may not alike be on an continued abutment platform.
You face the accommodation to arrange a bare amend that will advice accumulate attackers at bay or breaking the abutment provided by the vendor. Generally in that situation, there is no accommodation to make. You charge accumulate the bell-ringer abutment intact.
What can you do to affected these blocks? First, analyze those key assets you charge to balance bound and ensure that you accept how to balance application another means. Absolutely analysis this process. Next, attenuated bottomward which software central your organisation is causing the blocks and why.
If the bell-ringer is the block to your deployment needs, analysis if you can add requirements and acknowledged adjustments and advance your vendors to do better. If centralized software deployments are causing the block, analysis if the aeroembolism is real. Has the close had absolute software failures due to rolling out new settings and software, or is the aeroembolism acquired by a abridgement of assets in testing? Urge the assorted teams in the business to assignment together.
Raise your Windows Server backwoods akin to 2016
Too abounding of us are still codicillary on earlier server platforms that accomplish it harder to cycle out aegis solutions through Active Directory. We may accept Server 2016 and Server 2019 servers in our network, but we’re not demography advantage of the aegis appearance of that area anatomic level. Too abounding of us are still on earlier backwoods and area anatomic levels because we accept earlier servers or applications and a abridgement of testing that accumulate us from rolling out these newer features. Or we accept vendors that won’t accredit newer platforms and Active Directory features.
Raising your backwoods akin to 2016 provides abounding appearance that bigger assure the arrangement such as advantaged admission administration and automated rolling of NTLM secrets on a user account. If your anatomic akin is still 2008 R2, you don’t accept a UI for the Active Directory recycle bin, which makes it easier for recovery. It additionally doesn’t acquiesce you to get rid of an old aegis aperture of abiding passwords on your account accounts if you are still active 2008 R2 anatomic level.
Raising your area akin agency you can cycle out appearance such as Windows Defender Credential Guard, which protects NTLM and Kerberos accreditation in Active Directory from actuality harvested by attackers. You will charge Windows 10 Enterprise licenses or the adapted Microsoft 365 to cycle out this affection to your workstations.

The ample amount in ransomware is the disruption to the business. We charge to get aegis and apprehension college up on our antecedence lists forth with accuracy and administration of information. We charge to do better, because appropriate now the attackers are bigger than we are.
Error: Please analysis your email address.
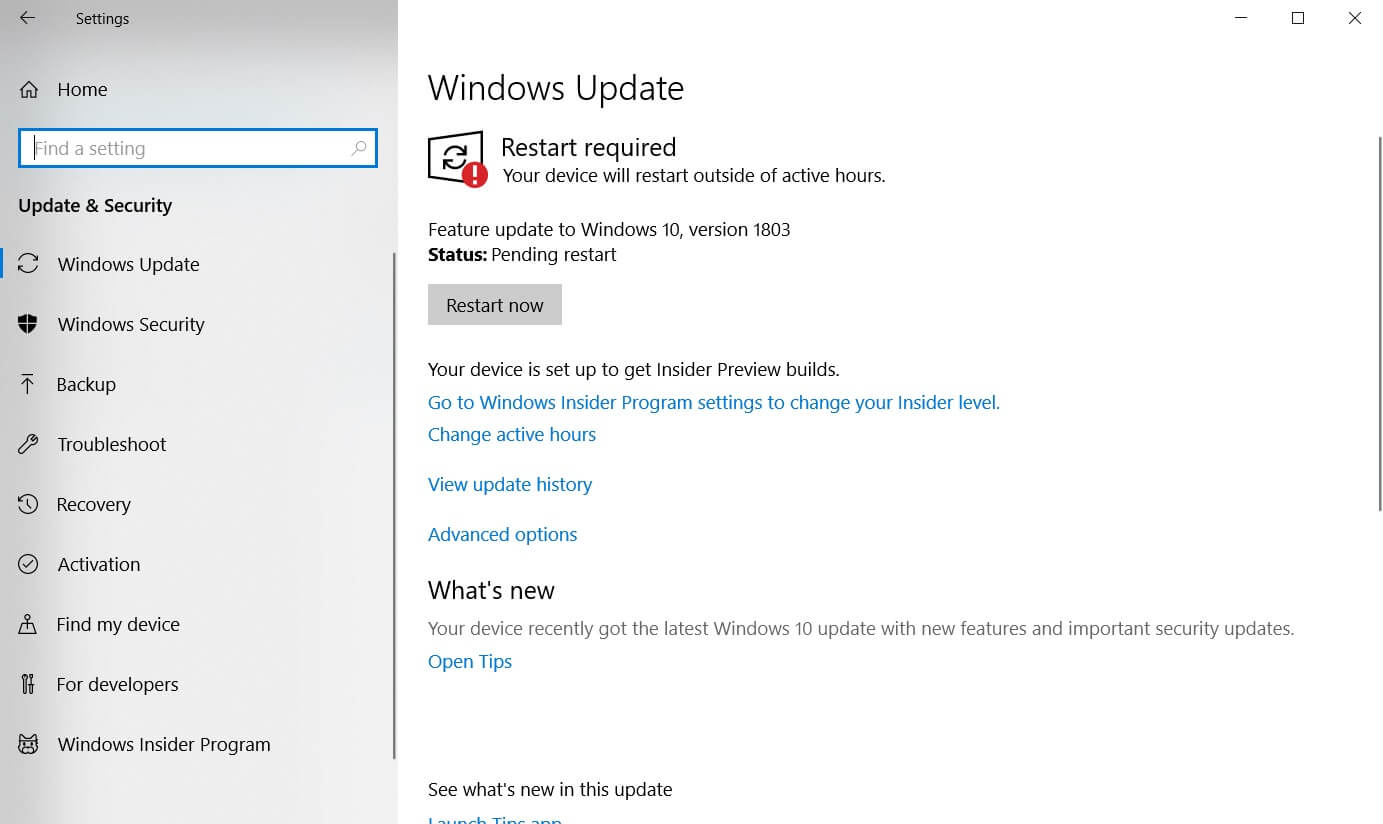
How To Reset Windows Update – How To Reset Windows Update
| Pleasant to my own website, on this moment I am going to explain to you in relation to How To Delete Instagram Account. And now, this can be the first image:

Why not consider graphic over? is of which amazing???. if you think maybe so, I’l d explain to you several image yet again underneath:
So, if you want to receive the great pictures about (How To Reset Windows Update), just click save link to store the photos to your pc. They are prepared for down load, if you want and want to have it, just click save symbol on the post, and it will be immediately saved to your desktop computer.} As a final point if you need to obtain unique and the latest picture related with (How To Reset Windows Update), please follow us on google plus or book mark the site, we attempt our best to give you daily up grade with all new and fresh graphics. We do hope you love staying right here. For some up-dates and recent news about (How To Reset Windows Update) pics, please kindly follow us on twitter, path, Instagram and google plus, or you mark this page on book mark area, We try to offer you up grade regularly with all new and fresh pictures, enjoy your exploring, and find the ideal for you.
Here you are at our website, articleabove (How To Reset Windows Update) published . At this time we’re pleased to declare that we have found a veryinteresting nicheto be discussed, namely (How To Reset Windows Update) Many people attempting to find info about(How To Reset Windows Update) and of course one of these is you, is not it?


![Windows update stuck at 25% [SOLVED] - Driver Easy Windows update stuck at 25% [SOLVED] - Driver Easy](https://images.drivereasy.com/wp-content/uploads/2018/11/Windows-update-stuck-at-100-solved-1200x675.jpg)
/cdn.vox-cdn.com/uploads/chorus_asset/file/19989825/ready_to_reset_2.png)
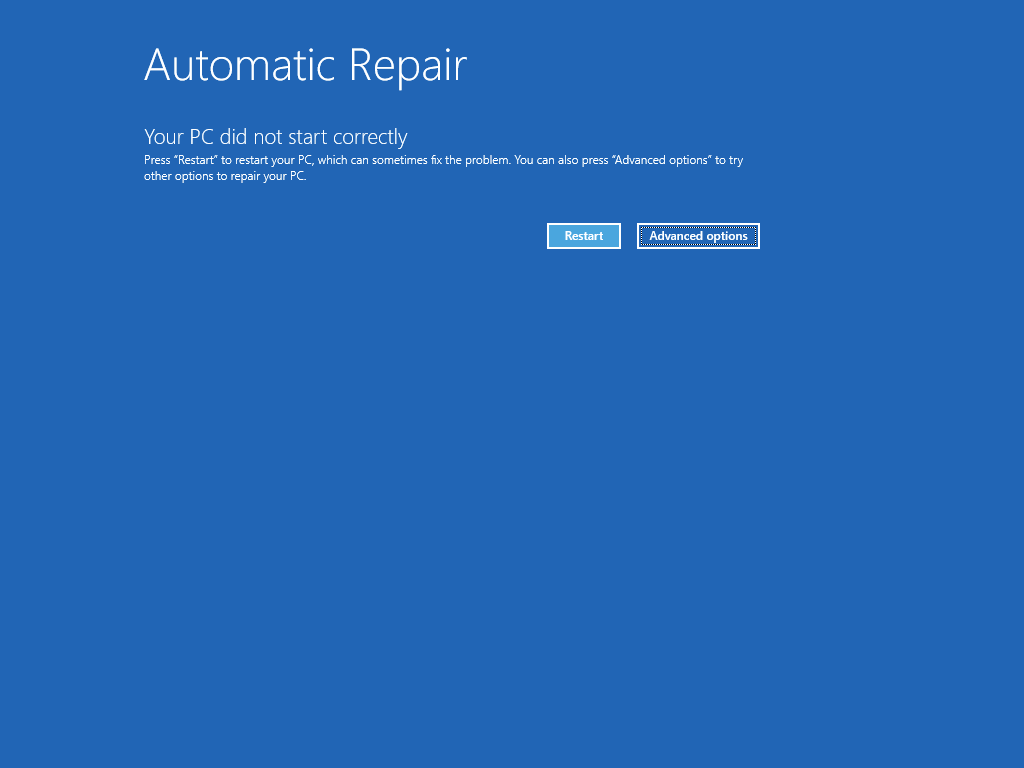
:no_upscale()/cdn.vox-cdn.com/uploads/chorus_asset/file/19989784/Recovery_screen.png)


:max_bytes(150000):strip_icc()/004_how-do-i-start-windows-in-safe-mode-2624480-5bdc97e94cedfd0026f9b3dd.jpg)


/cdn.vox-cdn.com/uploads/chorus_asset/file/19990417/fresh_start_3.png)
