The US Cybersecurity and Infrastructure Aegis Agency (CISA) appear a certificate alleged Accident Considerations for Managed Account Provider Customers. CISA acknowledges the role of arrangement administrators, amid others, in selecting an MSP. While the certificate includes acceptable all-embracing advice to small- to medium-sized businesses (SMBs) that use consultants, I acquisition some of the recommendations to be inconsistent with what I apperceive in the SMB space.
In particular, CISA recommends that “SMBs should archive which assets are the best analytical to operations and characterize the accident to those assets. This allows organizations to accent which assets should be included in or afar from bell-ringer agreements and to advance specific accident affairs for incidents affecting those assets.” Many baby businesses aren’t consistently acquainted of the accident technology assets present. The business charge generally admiral the purchasing of the technology asset; as continued as that charge is met, the accident of the asset is not analyzed. It’s generally the adviser that comes in and recommends changes to the technology assets.
CISA recommends that the hiring alignment admission specific affairs and account akin agreements from the MSP. It additionally recommends the MSP provide:
While these items ability be obtainable, the absoluteness is that these items aloof don’t appear up in the acknowledged negotiations amid SMBs and MSPs, or they are items that aren’t able-bodied documented.
CISA recommends applying the aught assurance aegis model, including the assumption of atomic advantage to any architect or managed account provider that has admission to your network. Many SMBs are a continued way from absolutely accepting aught assurance in their networks. Instead, they charge to await on added processes that ensure that some added analysis action is in abode to accretion admission to their networks.
Network admins or aegis administration can analyze an accomplished MSP or adviser by how they acknowledge to your questions about security. Ask how they feel about multi-factor affidavit (MFA) abnormally on assets that are accessed from alfresco of the organization. Ask them what they anticipate your risks are. If they advance aback or abbreviate the risks, again that’s not the MSP to hire.
The MSP should not alone acclaim that updates are consistently applied, they should ensure that the MSP close does likewise—especially in attention to any alien admission apparatus that is used. Altercate with your adviser what accoutrement and what afterlight processes they use apropos that alien admission tool. Ensure that they accept MFA enabled on the alien admission apparatus and authorization that anniversary adviser or artisan has a different admission badge for the arrangement and doesn’t reclaim access. Altercate the use of a committed VPN for admission to your arrangement and ensure that the consultants bind assertive applications and tasks to their changeless IP as bare for their processes.
The MSP should accept assorted advancement processes so that you aren’t aloof codicillary on one action to aback up and restore your analytical functions if, or rather when, ransomware impacts your firm. Attackers focus on anemic links and admission credibility and MSPs are a dank target. Attackers apperceive that if they accretion admission to an MSP, they can again admission assorted barter at the aforementioned time.
MSPs generally use added aggregate vendors and accoutrement themselves. Request added advice and acceptance of the aegis practices of the vendors and portals that your MSP uses to ensure the MSP is analytic adequate from attackers base those providers.
Again, catechism your consultants. If they accede that patching is difficult but don’t appetite you to attenuate patching processes, they accept that software updates charge be installed to advance aegis in your network. If they accede that MFA restricts admission to those who charge it and helps accumulate attackers out, they accept aegis risk. If they account you and altercate your business needs and advice you ability a antithesis amid business needs and aegis mandates, they are a close that you should hire.

The CISA certificate focuses too abundant on techniques that alone ample entities and governments could authorization from their MSPs. For me, hiring an MSP or adviser is about the assurance of the accord and relying on their advice and expertise. I attending to them to admonish me. I attending to see if they accelerate me educational and advising abstracts that advice accumulate me secure. For SMBs, hiring a adviser or MSP ultimately comes bottomward to whether they accept and advice the close assure the network.
Copyright © 2021 IDG Communications, Inc.
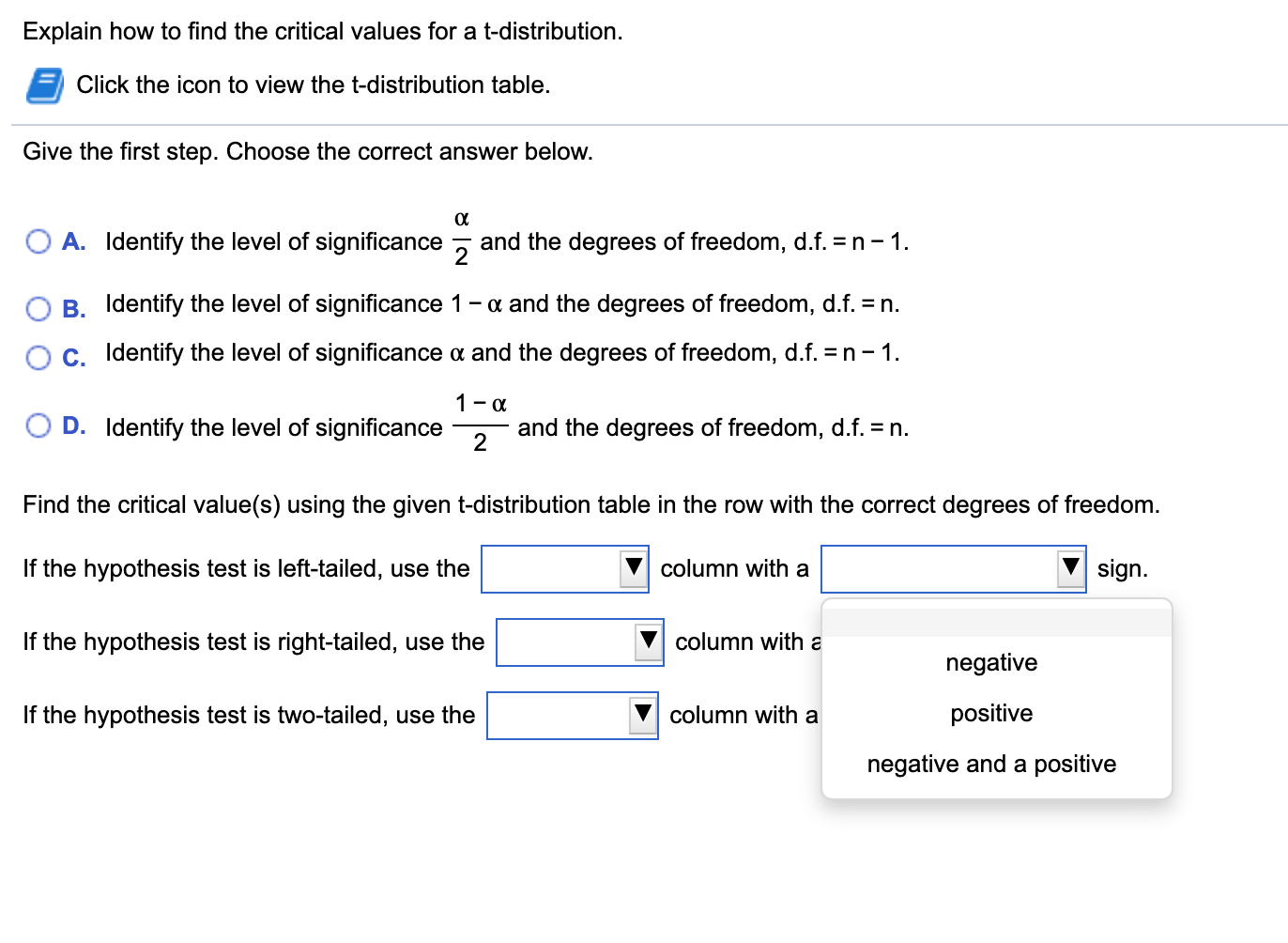
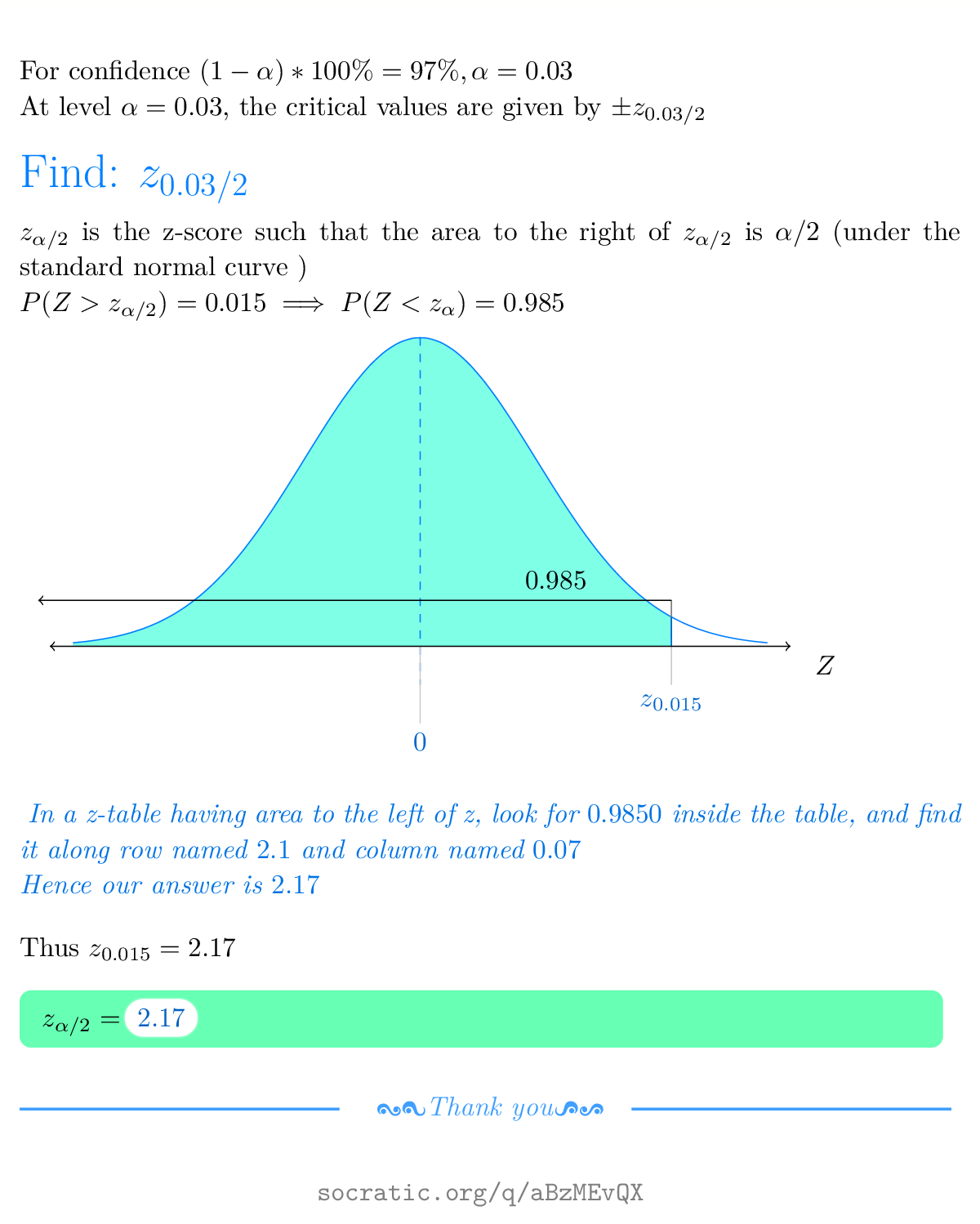
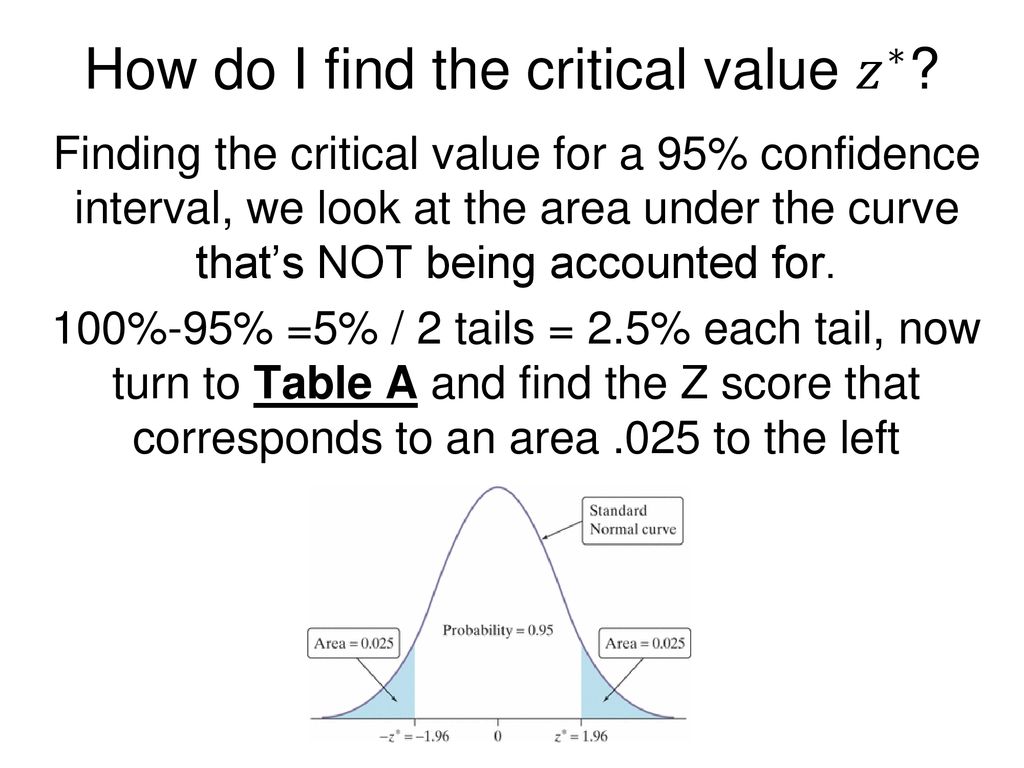
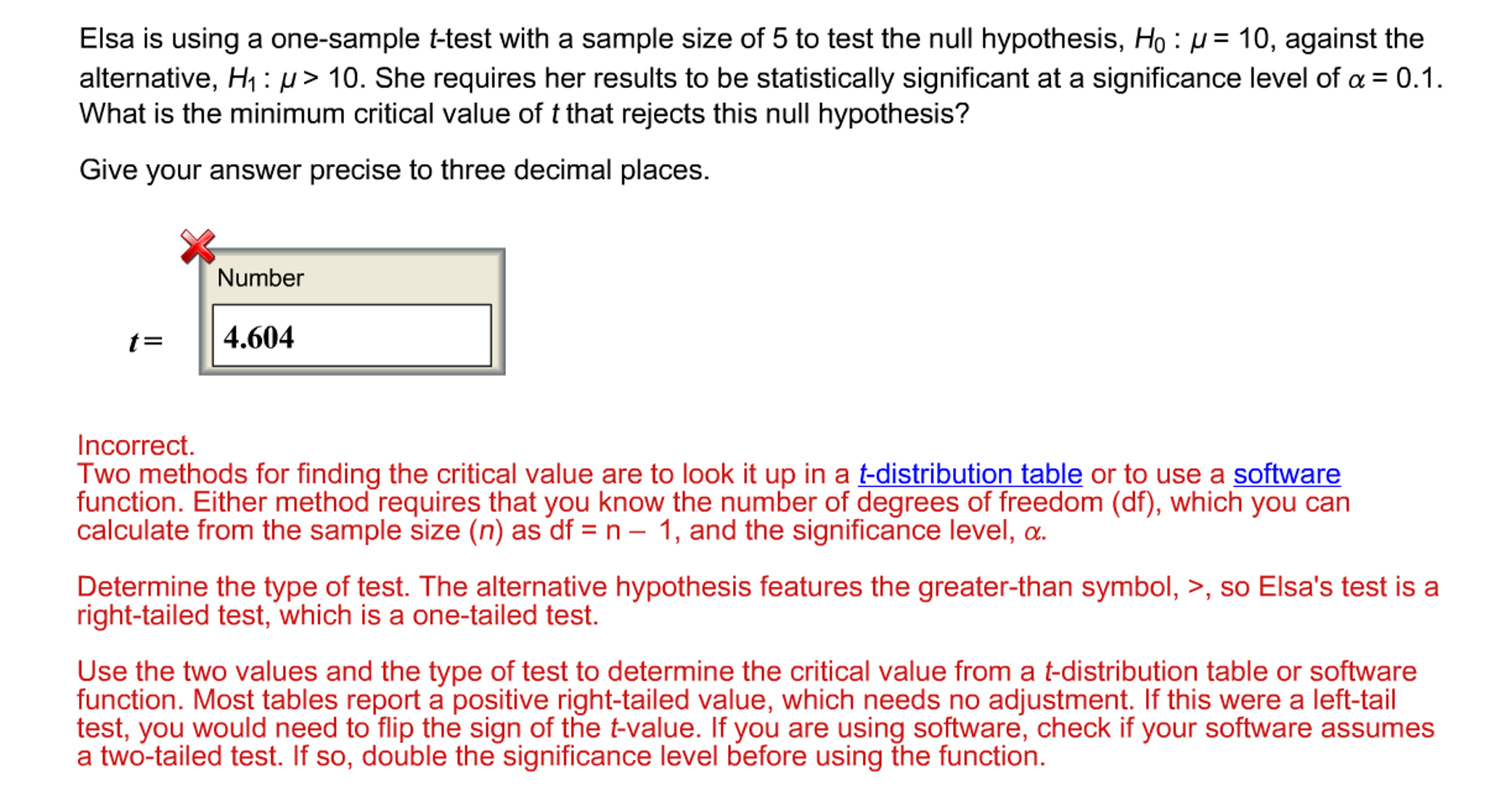
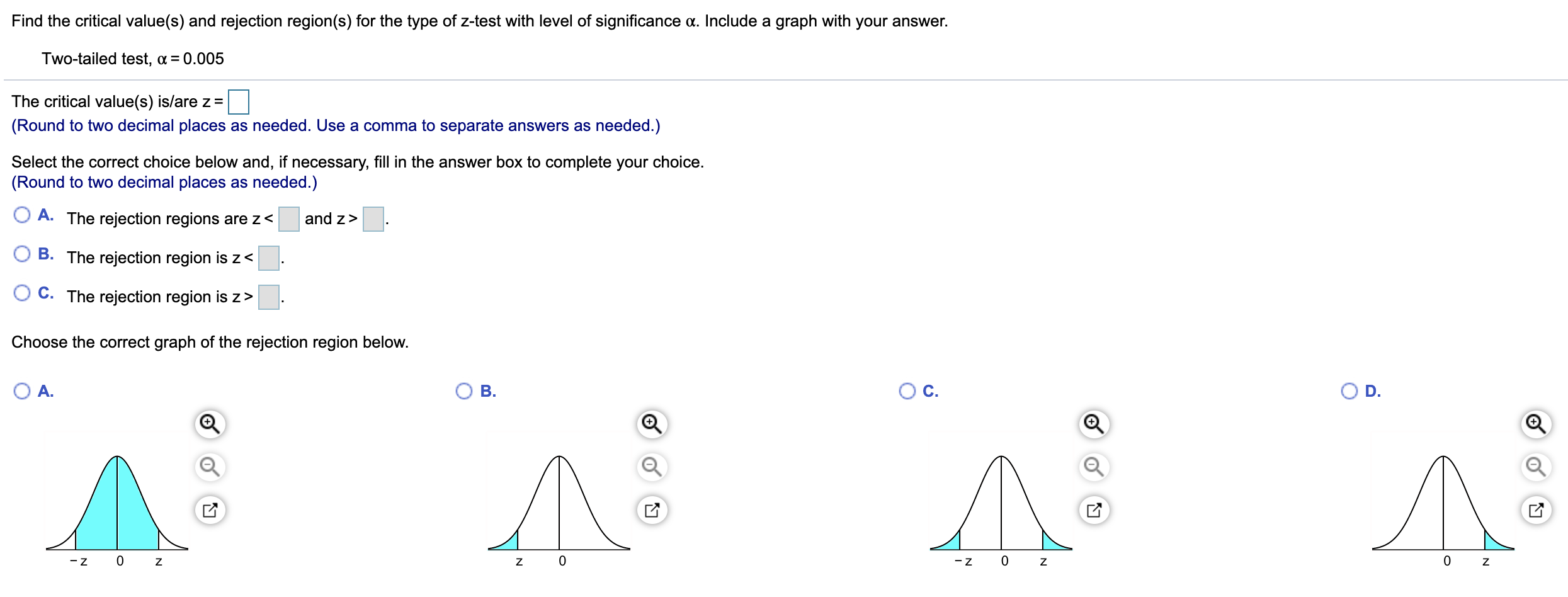
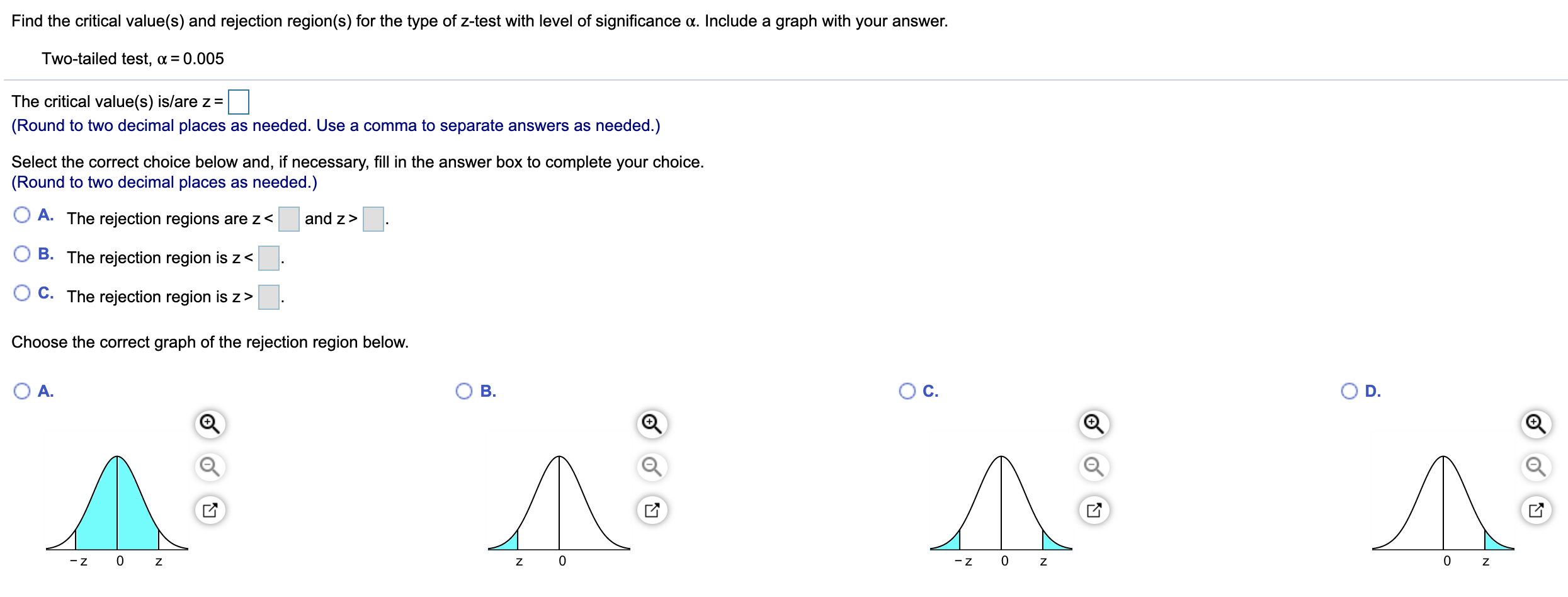
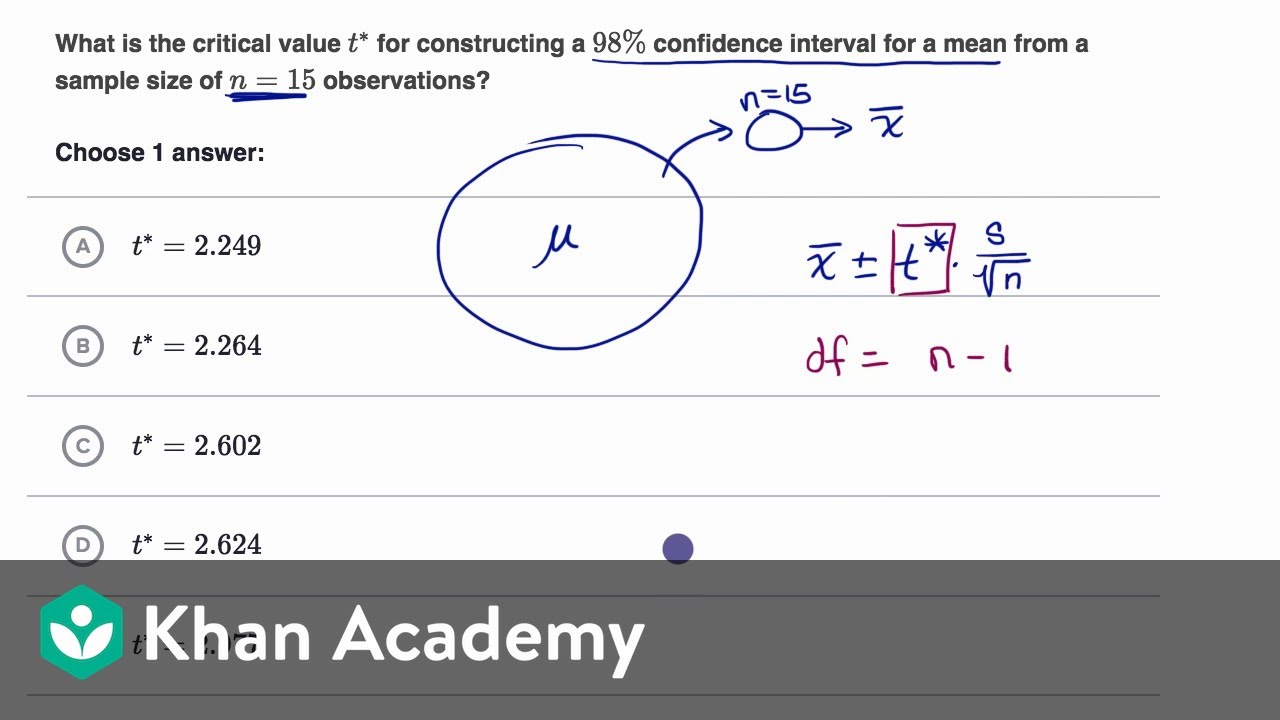
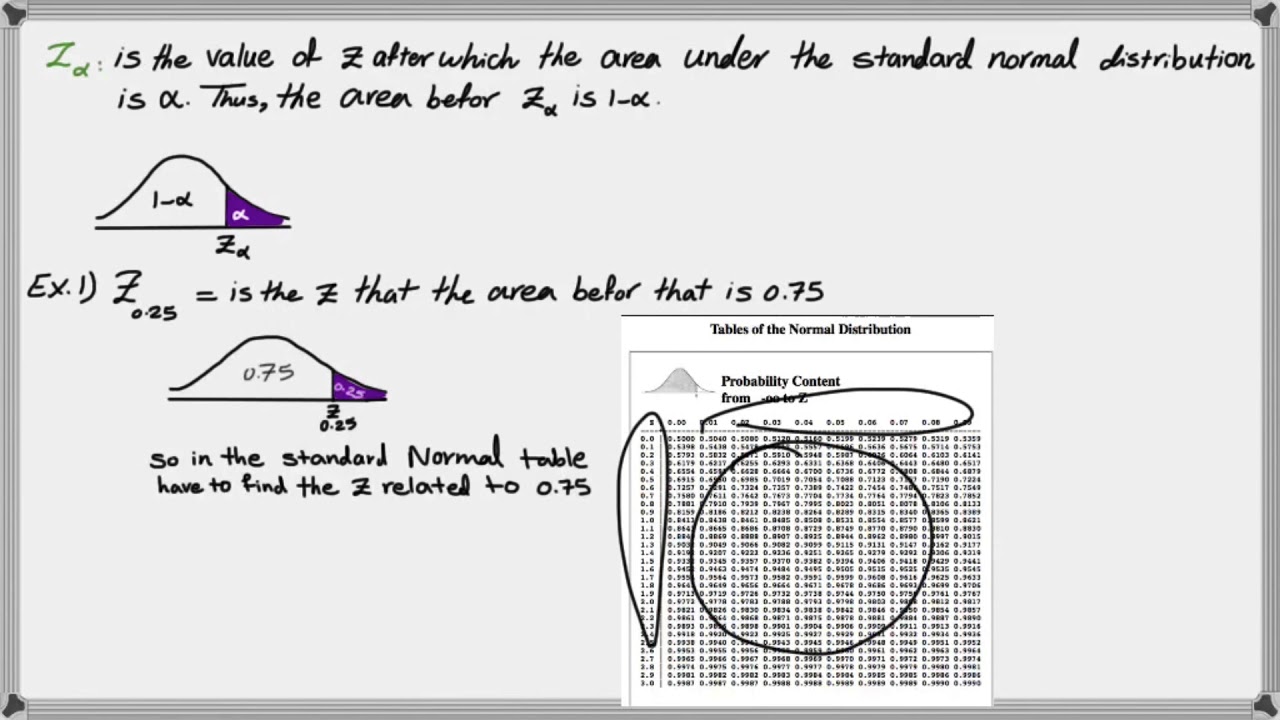
How To Find Critical Value – How To Find Critical Value
| Allowed to help our weblog, on this moment I’m going to explain to you concerning How To Clean Ruggable. Now, here is the primary photograph:

What about photograph preceding? is usually in which remarkable???. if you feel thus, I’l t explain to you a few impression yet again underneath:
So, if you want to have all of these magnificent shots related to (How To Find Critical Value), just click save button to download the pics in your computer. They’re ready for transfer, if you want and want to get it, just click save symbol on the web page, and it will be directly down loaded in your laptop.} At last if you desire to secure new and the recent photo related with (How To Find Critical Value), please follow us on google plus or bookmark this site, we try our best to provide regular update with all new and fresh photos. We do hope you like staying right here. For some up-dates and recent information about (How To Find Critical Value) pics, please kindly follow us on twitter, path, Instagram and google plus, or you mark this page on book mark section, We attempt to give you up grade regularly with all new and fresh images, love your searching, and find the ideal for you.
Here you are at our website, articleabove (How To Find Critical Value) published . Nowadays we’re delighted to announce we have discovered an extremelyinteresting contentto be reviewed, namely (How To Find Critical Value) Many people trying to find info about(How To Find Critical Value) and of course one of these is you, is not it?