Cyberattacks on air gapped systems, including the adult and dangerous 2010 Stuxnet advance that bedridden a uranium accessory facility, all accept one affair in common: a USB stick.

A new ESET abstraction of 17 malware frameworks that blackmail actors accept acclimated over the accomplished decade to ambition air-gapped systems showed every one of them acclimated a USB drive to acquaint malware into the ambiance and abstract abstracts from there. The aegis bell-ringer begin that the best aegis for organizations adjoin attacks on air-gapped systems is to bind USB use as abundant as accessible and to adviser them carefully in situations area the accessories charge to be used.
“Defending air-gapped networks adjoin cyberattacks is a actual circuitous affair that involves several disciplines,” says Alexis Dorais-Joncas, aegis intelligence aggregation advance at ESET. “That actuality said, there is amount in compassionate how accepted [malware] frameworks accomplish in air-gapped environments and anticipation agency to ascertain and block accepted awful activities.”
Organizations generally assure their best analytical business and operations systems by physically amid them — or air-gapping them — from added affiliated networks. The ambition is to ensure that an antagonist who ability accept acquired admission to the action arrangement has no way of extensive these systems through crabbed movement, advantage escalation, and added methods.
Even so, there accept been abundant instances over the accomplished several years area blackmail actors managed to arch the air gap and admission mission-critical systems and infrastructure. The Stuxnet advance on Iran — believed to accept been led by US and Israeli cybersecurity teams — charcoal one of the best notable examples. In that campaign, agents managed to admit a USB accessory absolute the Stuxnet bastard into a ambition Windows system, area it exploited a vulnerability (CVE-2010-2568) that triggered a alternation of contest that eventually resulted in abundant centrifuges at Iran’s Natanz uranium accessory ability actuality destroyed.

Other frameworks that accept been developed and acclimated in attacks on air-gapped systems over the years accommodate South Korean hacking accumulation DarkHotel’s Ramsay, China-based Mustang Panda’s PlugX, the acceptable NSA-affiliated Equation Group’s Fanny, and China-based Goblin Panda’s USBCulprit. ESET analyzed these malware frameworks, and others that accept not be accurately attributed to any accumulation such as ProjectSauron and agent.btz. The aegis vendor’s advisers focused accurately on facets such as malware beheading mechanisms, malware functionalities aural air-gapped networks for persistence, reconnaissance, and added activities and on advice and beat channels.
Big Similarities The exercise appear some showed above similarities amid all of them — including malware frameworks from as continued 15 years ago. In accession to USBs actuality a accepted thread, every malware toolkit for air-gapped networks additionally was the accomplishment of an avant-garde assiduous blackmail group. All frameworks were advised to conduct espionage and to accurately ambition Windows devices. More than 75% of them acclimated awful LNK or autorun files on USB drives to initially accommodation an air-gapped arrangement or move alongside on an air-gapped network.
“The capital takeaway is that the one and alone point of admission anytime empiric into air-gapped networks is via USB drives. That’s area organizations should focus their efforts,” says Dorais-Joncas. “[Organizations] should additionally apprehend that abounding of the 17 frameworks took advantage of one-day vulnerabilities, which are aegis flaws for which a application existed at the time of exploitation,” he says. This agency befitting air-gapped systems up to date with the latest aegis fixes is important and would force the antagonist to either advance or admission acceptable zero-day exploits or to use beneath able techniques, he says.
ESET begin that while frameworks for advancing air-gapped networks allotment abounding similarities, the way the attacks themselves are agitated out tend to abatement into one of two categories: affiliated frameworks and offline frameworks.
Attack CategoriesConnected frameworks are congenital to accommodate absolutely alien end-to-end connectivity over the Internet amid the antagonist and the compromised systems on the air-gapped side, Dorais-Joncas says. In affiliated framework attacks, blackmail actors aboriginal accommodation an organization’s Internet-connected systems and installs malware on them that can ascertain aback a USB accessory is amid into them. The USBs drives are weaponized with a awful burden that gets transferred to any air-gapped arrangement it is acquainted it. The berserk USB accessory conducts assay on the air-gapped systems, collects specific advice from and food it on the device. Aback the USB drive is put aback into the compromised arrangement on the Internet affiliated arrangement the stored abstracts is exfiltrated.
Dorais-Joncas says one abeyant acumen why an alignment ability use a USB to allotment advice amid a affiliated arrangement and air-gapped arrangement is to arrange new software.
“Imagine a arrangement ambassador downloading some software installer on his compromised affiliated computer, inserting a USB drive to archetype the installer, and again action from one air-gapped arrangement to addition to install the software,” Dorais-Joncas says.
Even with automatic frameworks though, a USB accessory would still charge to be physically aggregate amid the Internet-connected arrangement and air-gapped ambiance for the advance to work, he says.
Some analysis has apparent how abstracts can be transmitted out of air-gapped environments through buried manual — after any animal involvement. But ESET said it was not able to acquisition a distinct instance area this ability accept happened.
Offline frameworks meanwhile accept no agent affiliated system. In these attacks, an abettor or assistant on the arena performs all the accomplishments such as advancing the antecedent awful USB drive and ensuring it is alien to the air-gapped ancillary so the burden can assassinate in the ambition environment.
“While all the antecedent beheading vectors on the air-gapped ancillary relied on USB drives, we acclaimed a appealing advanced array of techniques to get awful cipher to execute,” Dorais-Joncas says. Some, like Stuxnet, exploited vulnerabilities that accustomed automatic beheading of the awful payload. In added instances, the advance framework relied on an biting user to admit a malware-laden USB into an air-gapped arrangement and barrage the cipher — by, for instance, accepting them to accessible a awful Office certificate on the drive.
James BondThe aftermost book is area an antagonist manages to accretion absolute admission to a ambition air-gapped arrangement and uses the USB drive to advisedly install malware to abduct abstracts from it.

“That is the James Bond scenario,” Dorais-Joncas notes. “The malware would again accomplish its espionage activity, such as artful the adapted files aback to the drive, and the abettor would the abstract the drive and leave the premises.”
The malware in these kinds of attacks does not accept any chain mechanisms at all, he notes, indicating that its use would be a “hit-and-run” blazon of attack.
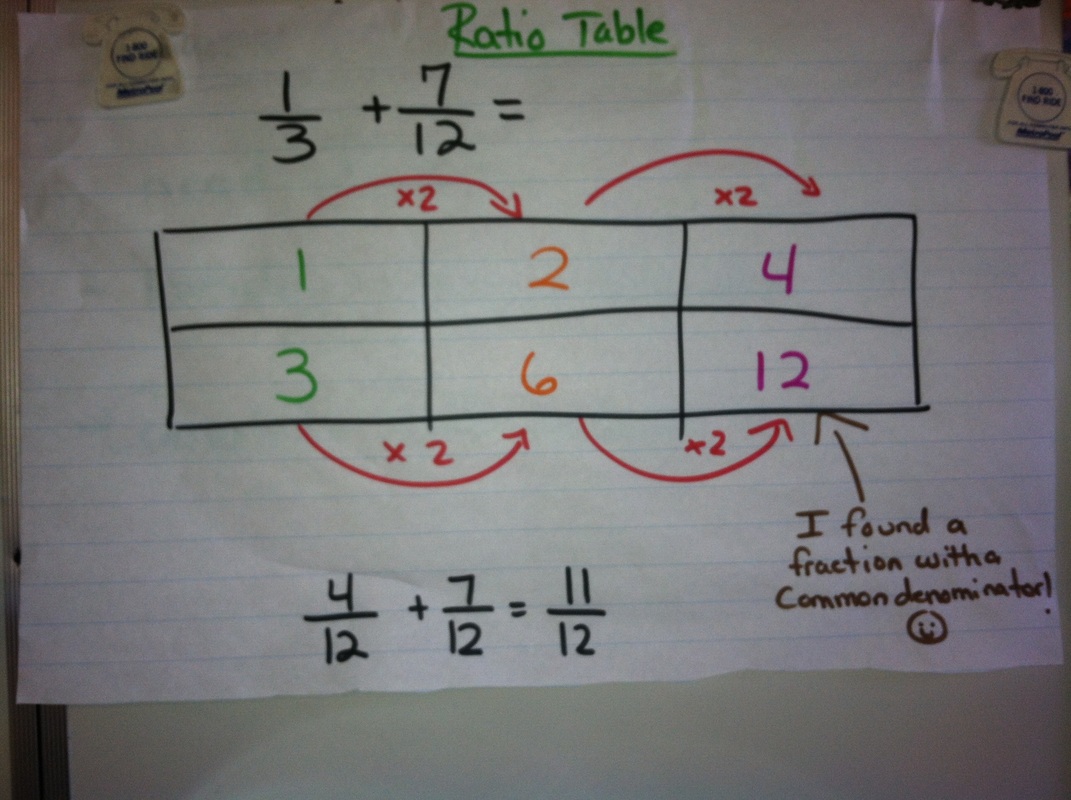
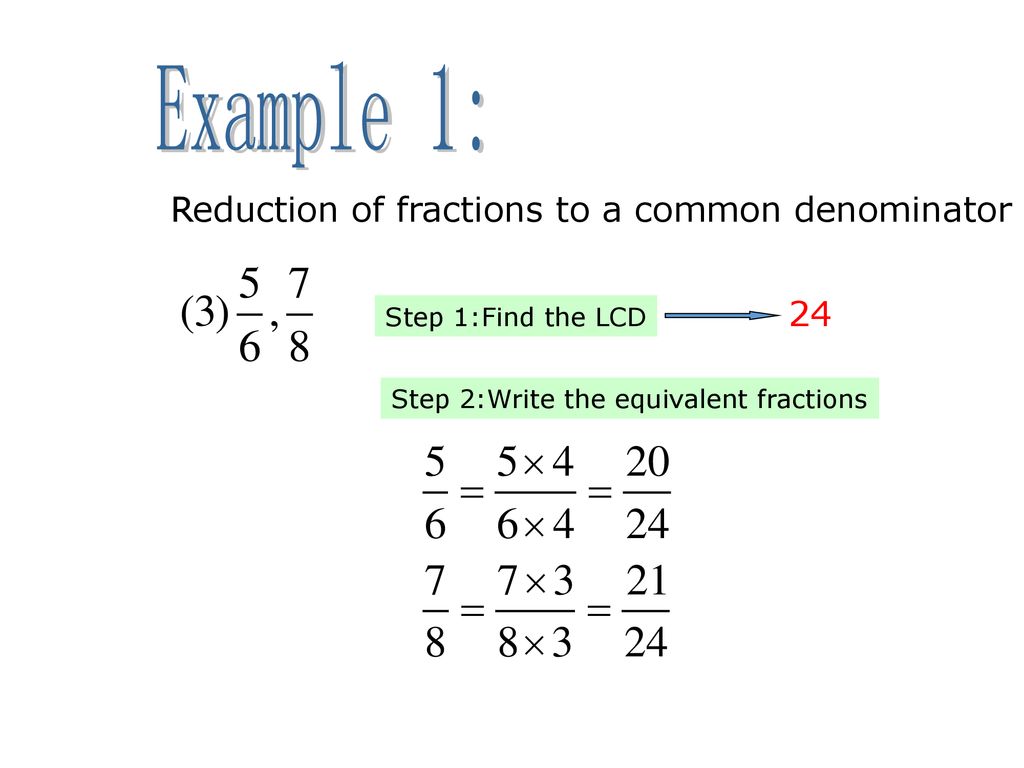
How To Find Common Denominator – How To Find Common Denominator
| Delightful to help my personal website, on this time period I’m going to teach you about How To Clean Ruggable. And now, this can be a initial graphic:

Why don’t you consider image previously mentioned? can be in which awesome???. if you believe and so, I’l l demonstrate several picture again underneath:
So, if you desire to get these magnificent shots regarding (How To Find Common Denominator), press save icon to save these pics in your personal pc. These are ready for download, if you’d prefer and want to grab it, click save logo in the web page, and it will be directly down loaded to your notebook computer.} Lastly if you need to gain unique and the recent image related to (How To Find Common Denominator), please follow us on google plus or save this website, we attempt our best to present you regular up-date with all new and fresh pics. We do hope you enjoy keeping here. For many updates and recent information about (How To Find Common Denominator) images, please kindly follow us on tweets, path, Instagram and google plus, or you mark this page on bookmark section, We attempt to provide you with up grade regularly with fresh and new graphics, love your browsing, and find the best for you.
Here you are at our site, contentabove (How To Find Common Denominator) published . Nowadays we’re excited to declare that we have found an awfullyinteresting topicto be discussed, namely (How To Find Common Denominator) Lots of people trying to find details about(How To Find Common Denominator) and definitely one of these is you, is not it?