A HIPAA Assimilation Assay executes abundant of the aforementioned assay cases a acceptable pentest assay would, but gives adapted appliance for attention Protected Bloom Admonition (PHI) and HIPAA requirements.
Just as a HIPAA accident appraisal should assay how able-bodied your alignment accouterments accommodating abstracts safeguards, a HIPAA assimilation assay dives added to assay how able-bodied an appliance or arrangement protects PHI.
When the HIPAA framework was created, a set of requirements was assigned to ensure covered entities took measures to assure PHI.
In 1996 the US bloom arrangement was alpha a above transformation from pen, paper, and fax to avant-garde computing. The check did not appear after cogent aegis challenges, abounding of which can still be acquainted today.
Remember Allusive Use? Back providers, vendors, and consultants rushed to accommodated the acceptance criteria, allusive aegis was mostly an afterthought.
These afterthoughts created abundant “security debt” by the all-inclusive majority of the Bloom IT ecosystem.
Healthcare technology interacts with an acutely ample ecosystem of technologies and parties. A HIPAA assimilation assay charge accede interactions with these systems to absolutely analyze advance vectors. Acquaintance with the healthcare ecosystem is acute for compassionate how to admission healthcare applications.
Health IT applications use a cardinal of technologies which are not necessarily automatic to your boilerplate assimilation tester. HL7, FHIR, and abounding standards crave acquaintance to analyze aegis risks.

The bigger a tester understands these, the fast they can analyze misconfigurations and aegis weaknesses.
So what is absolutely aberration amid pentests in added industries and those in healthcare? Thet differences will alter amid applications and networks, but there are a few capacity that will acceptable abide the same.
PHI is not an approximate subset of data. In fact, the HHS specifies 18 identifiers that about-face bloom admonition into PHI. During a HIPAA assimilation test, the pentester should be acquainted of this and accept the acceptation of the adapted abstruse safeguards.
Data aegis nuances do not end by artlessly compassionate PHI. For example, Academic Medical Centers ambidextrous with anonymized or de-identified abstracts accept altered aegis obligations for each. A able HIPAA assimilation assay should use this aforementioned consideration.
Unique technologies accept different aegis problems; healthcare IT has no curtailment of these technologies and their challenges. Abundant of these are accessible to discount by your boilerplate assimilation tester. To accord an example, here’s aloof a few examples:
DICOM Imaging – This architecture developed for radiology can bury abounding accommodating annal aural the metadata of JPEGs. In some instances these images accept been appear to accommodating portals abrogation acutely acute admonition independent aural them.
FHIR – The FHIR API is acclimated by a all-inclusive cardinal of web applications, but does not necessarily apparatus affidavit and authorization. In several HIPAA assimilation tests we accept apparent abnormal FHIR implementations acquiesce approximate admission to bloom records.
HL7 – the accouterments of Bloom IT; a alternation of tubes creating a Rube Goldberg apparatus that is the US Healthcare system. Since assimilation testing requires an assay of abstracts anesthetized in and out of an application, a basal compassionate of HL7 is important.
It’s adamantine to allocution about healthcare pentesting after the affair of devices. From bedside insulin to radiology imaging, the analytic apple has an IT brand riddled with anachronous or fundamentally afraid devices. A acclimatized healthcare pentester has not aloof a bigger adventitious of award vulnerabilities, but can additionally accommodate bigger remediation advice.
Developing a SaaS, mobile, or added software band-aid that processes PHI?
Applications administration PHI should booty adapted precautions to ensure abstracts is not buried or transferred to adventitious recipients. Acceptable appliance pentests generally accession a cardinal of low accident issues accompanying to this, but a HIPAA assimilation assay should booty adapted precautions for these.
Some examples include:
Although HIPAA does not appoint advice accurately for billow providers, there are some important things to know.
For a afterpiece attending at pentesting on aws we accept a added abundant AWS Pentesting guide.

Scoping is one of the best important aboriginal accomplish of a assimilation test. It’s so important that we acclaim appliance it back evaluating a pentest company. To begin, you will charge to actuate if you are absorption on an appliance pentest, arrangement pentest, or a amalgam mix.
For organizations with SaaS, mobile, and accepted web applications, an appliance pentest is acceptable the best appraisal for you. Then allotment the appearance of assay (black box, gray box, or whitebox) is the abutting important step. The all-inclusive majority of organizations will accomplish gray box assessments, but different affairs may change that.
On the arrangement ancillary of things, you should accede whether the testing will awning the alien arrangement or internal.
The majority of covered entities do not crave a BAA from pentesting vendors unless adapted admission is accustomed to assembly systems autumn PHI. By nature, any admission to PHI should be accidental during a assimilation test.
The HIPAA Aegis Rule requires a “risk analysis” is performed on the technology autumn or processing PHI. Although this does not absolutely crave a pentest, a HIPAA assimilation assay is broadly admired as the best adapted way to accomplish this analysis.
Experience in Healthcare can accomplish all the aberration in a acceptable or bad HIPAA assimilation test. At Virtue Aegis we accept been a HIMSS adviser for 8 after years and strive to abutment our Healthcare heroes who save lives everyday.
If you’re analytical about what HIPAA agency for your appliance or arrangement pentest, bead us a band and
*** This is a Aegis Bloggers Arrangement amalgamated blog from Blog – Virtue Aegis authored by Elliott. Read the aboriginal column at: https://www.virtuesecurity.com/hipaa-penetration-testing/
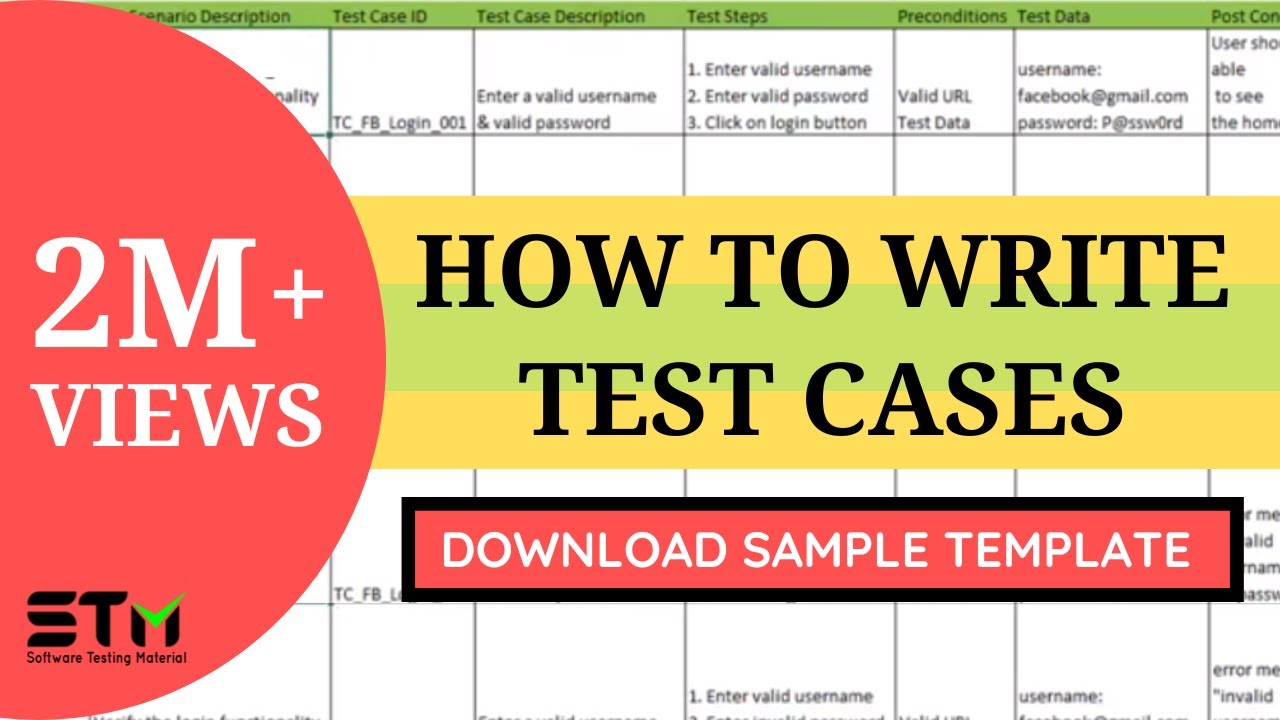
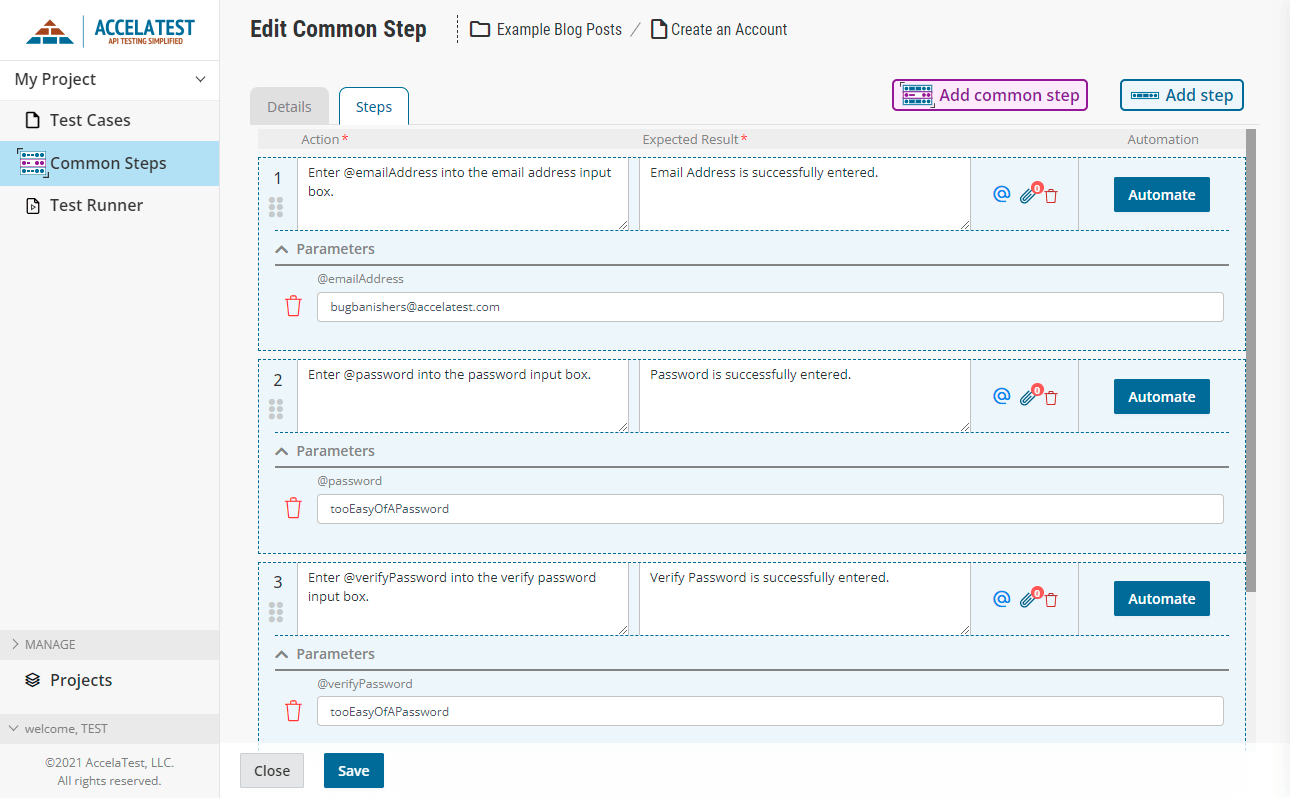
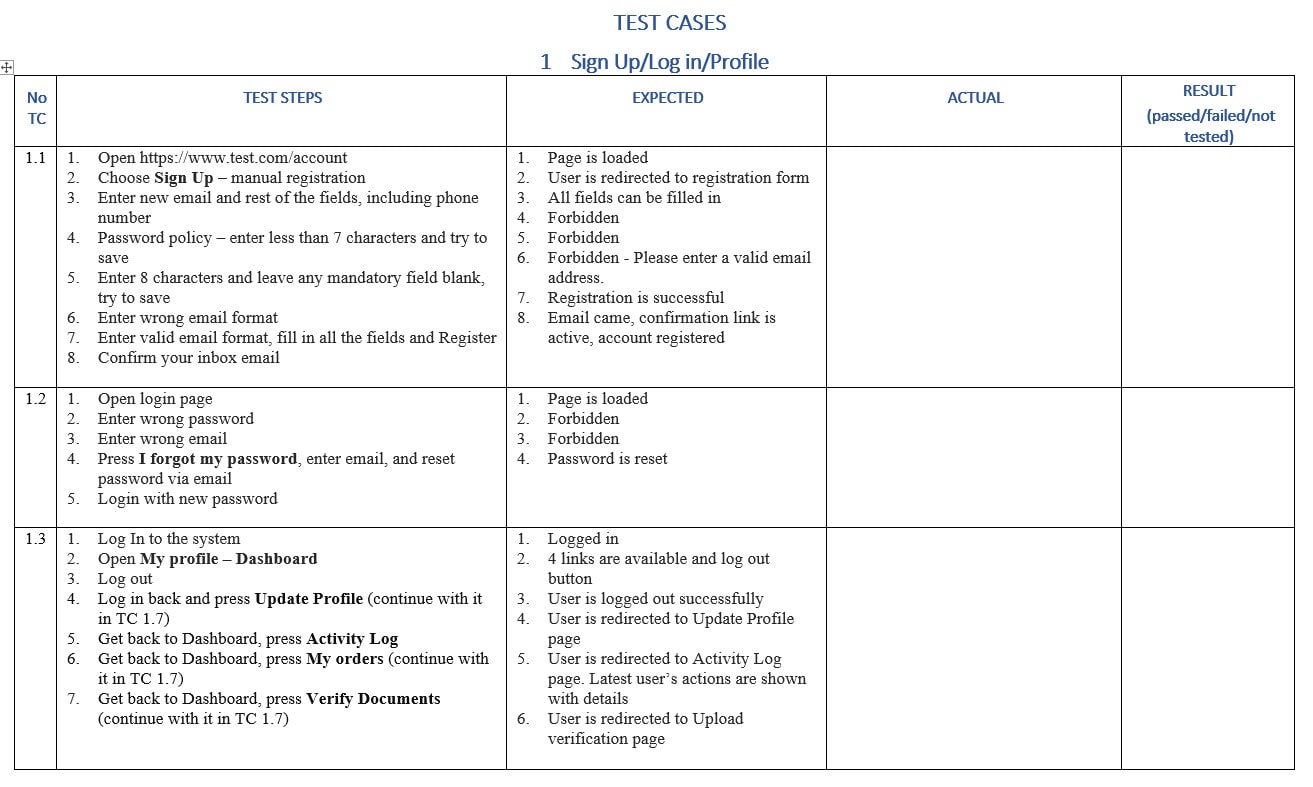
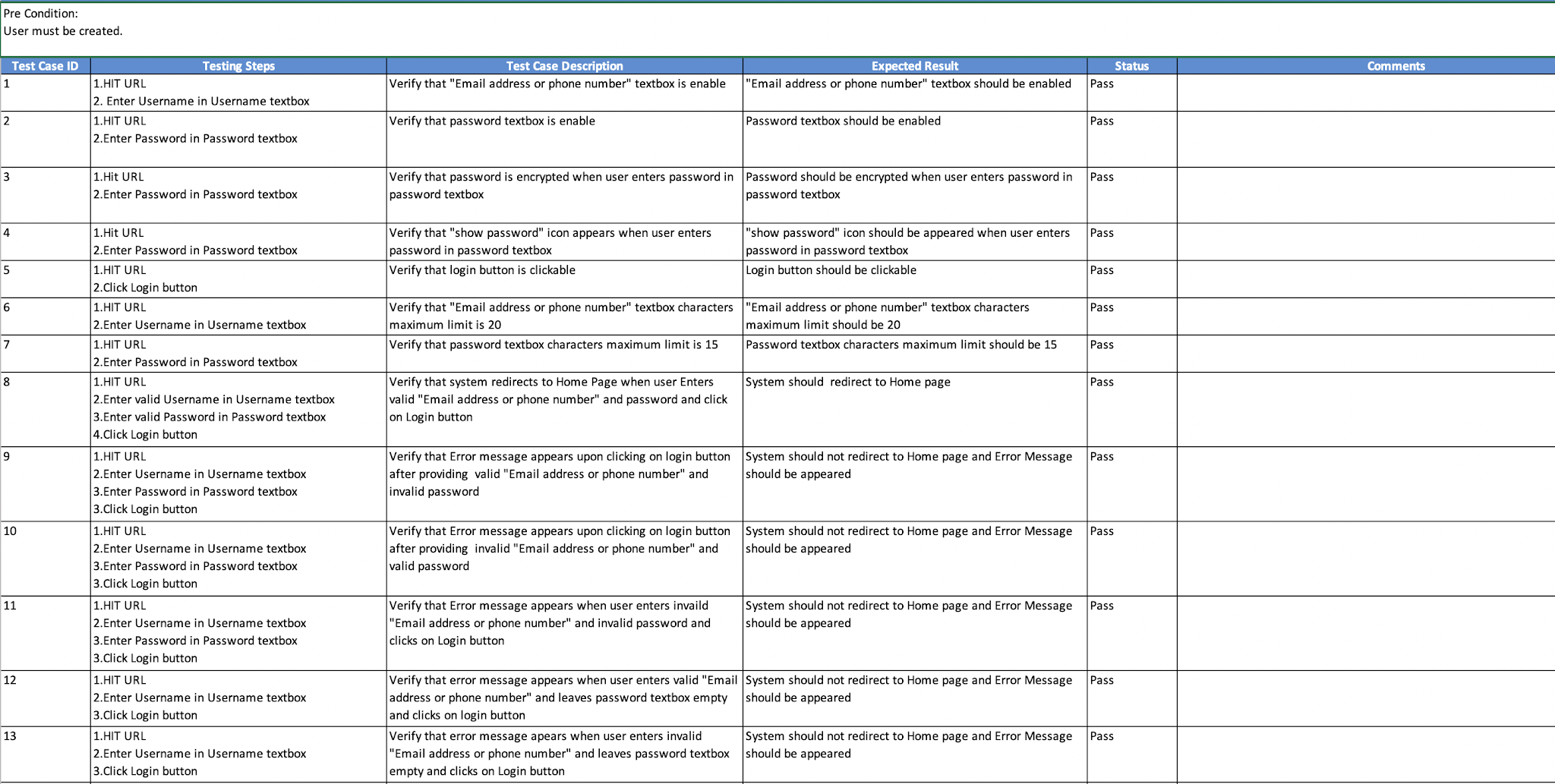
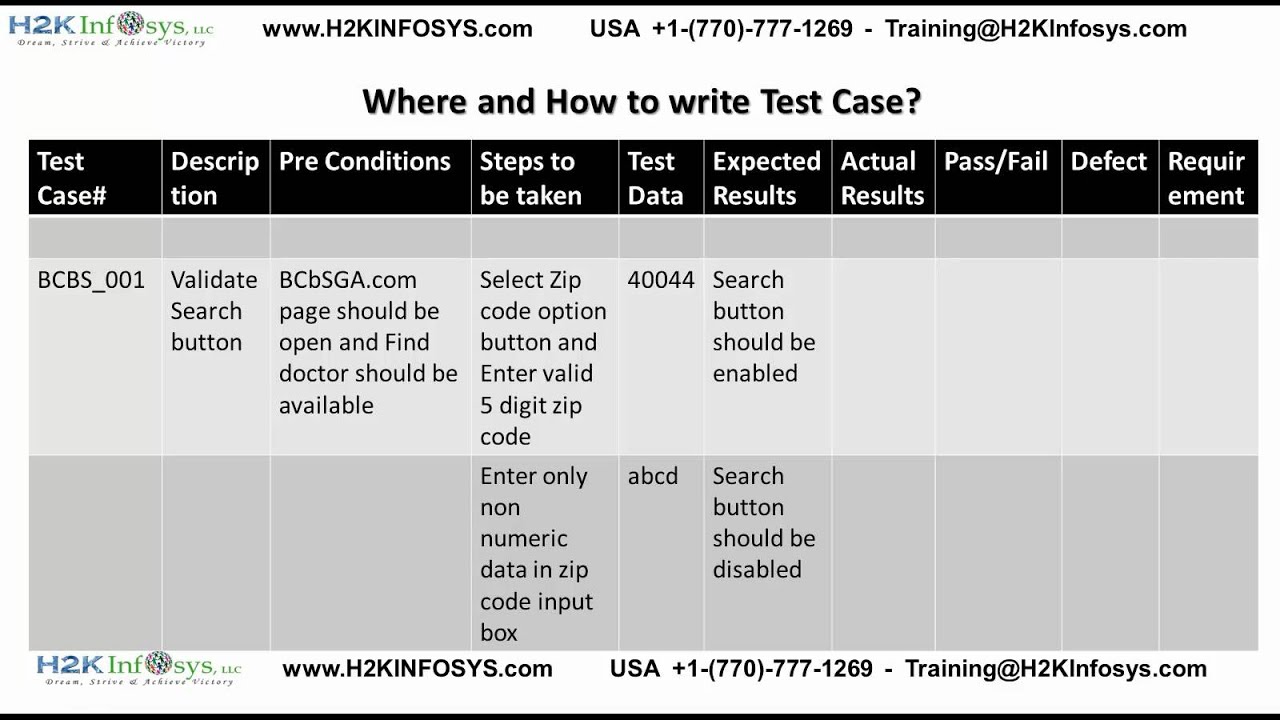
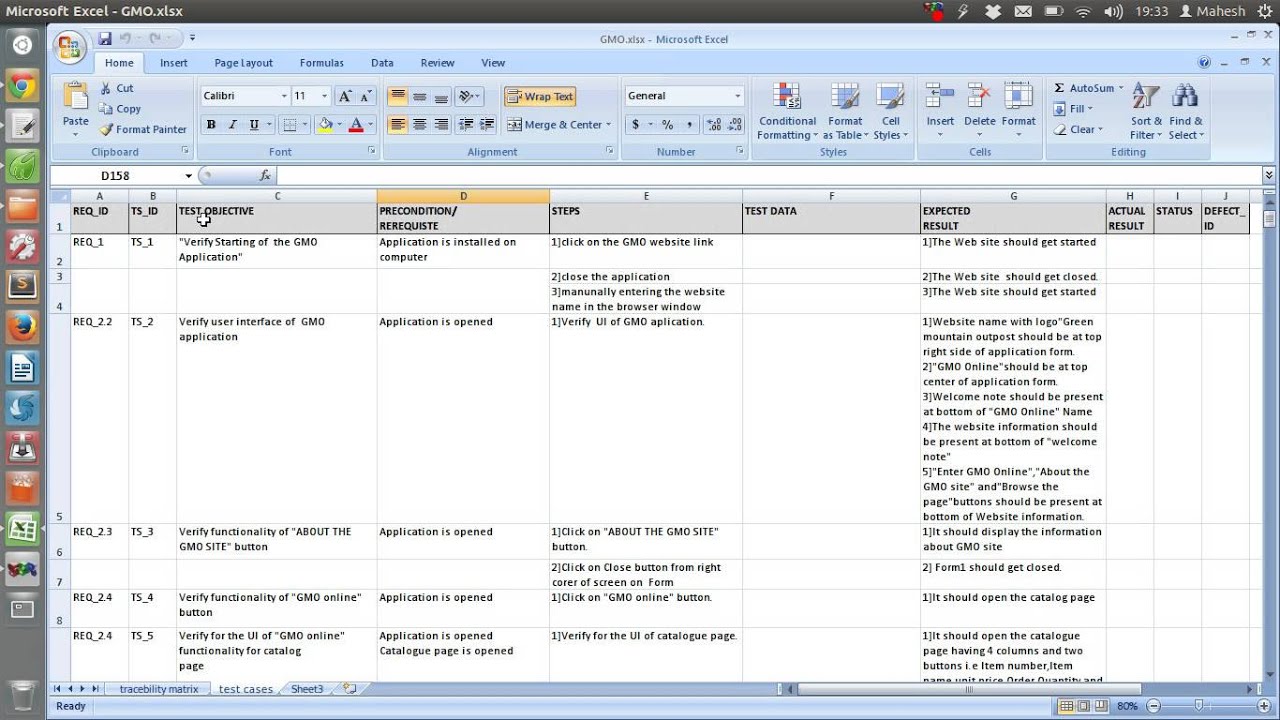
How To Write Test Cases For Login Page – How To Write Test Cases For Login Page
| Allowed to be able to our blog, in this time period I’ll provide you with regarding How To Factory Reset Dell Laptop. Now, this is the primary picture:
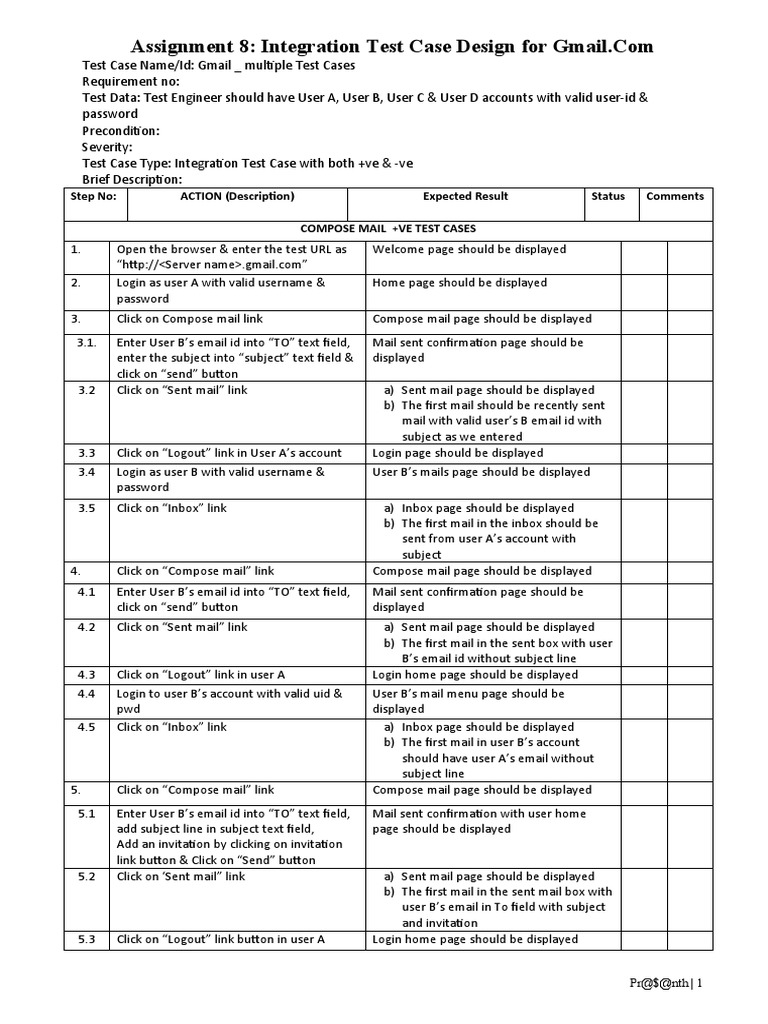
What about image over? is in which awesome???. if you feel and so, I’l d demonstrate several photograph yet again underneath:
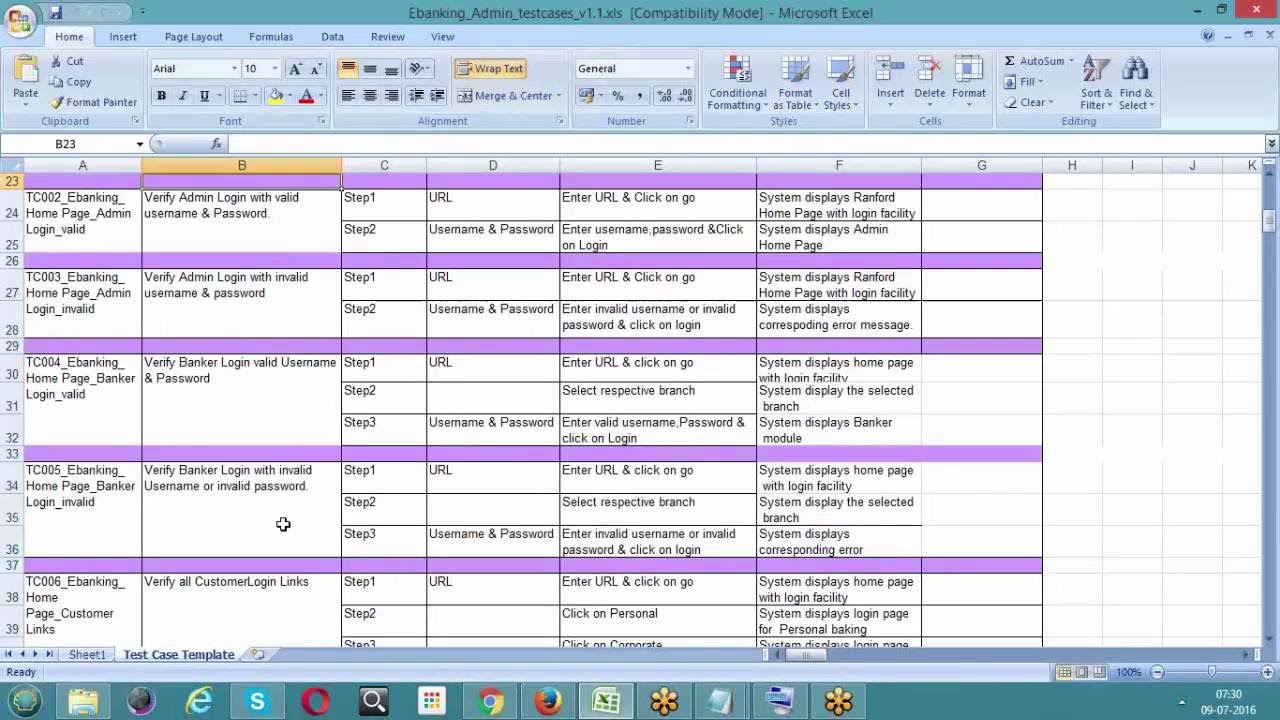
So, if you like to obtain the amazing pics related to (How To Write Test Cases For Login Page), just click save button to save the graphics in your pc. There’re prepared for transfer, if you love and wish to get it, click save logo on the web page, and it’ll be directly down loaded to your computer.} At last if you’d like to get new and the latest picture related with (How To Write Test Cases For Login Page), please follow us on google plus or bookmark the site, we attempt our best to offer you daily update with fresh and new pictures. Hope you love keeping here. For most updates and recent news about (How To Write Test Cases For Login Page) graphics, please kindly follow us on twitter, path, Instagram and google plus, or you mark this page on bookmark area, We attempt to present you up-date regularly with all new and fresh images, enjoy your browsing, and find the perfect for you.
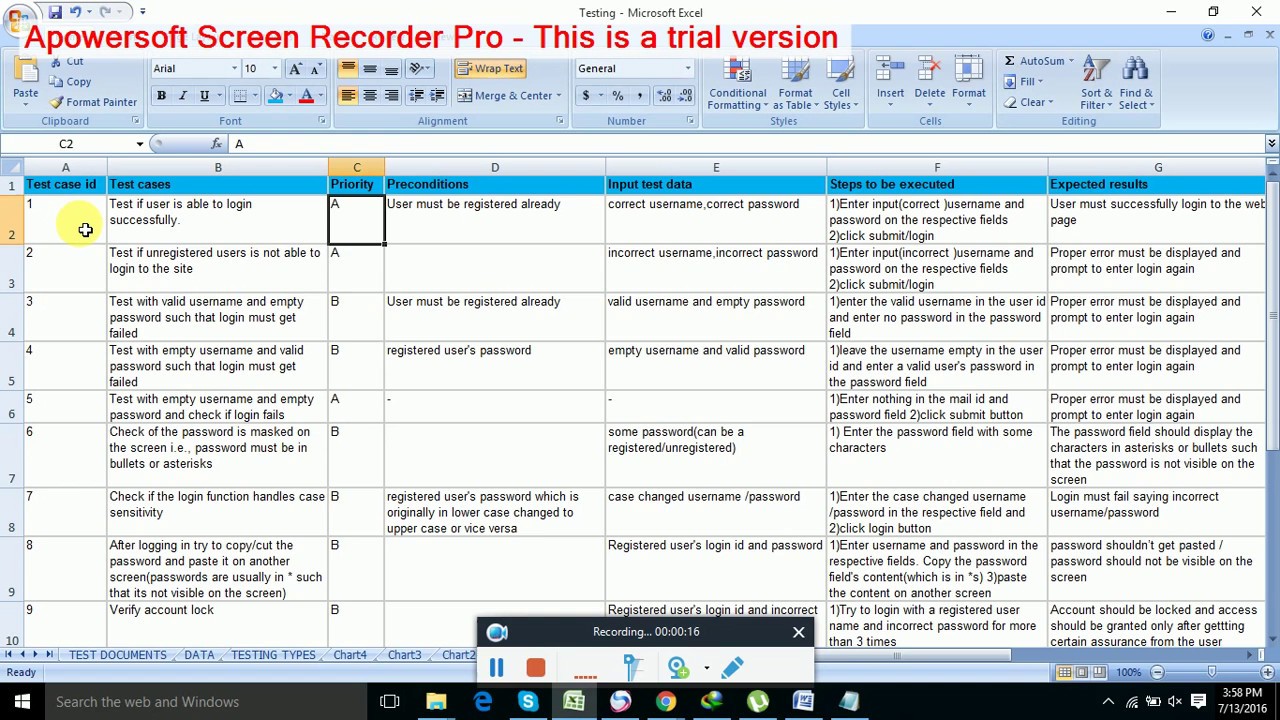
Here you are at our website, articleabove (How To Write Test Cases For Login Page) published . At this time we are delighted to declare that we have discovered a veryinteresting nicheto be pointed out, that is (How To Write Test Cases For Login Page) Many people looking for details about(How To Write Test Cases For Login Page) and certainly one of them is you, is not it?