To breach a footfall avant-garde of cyber defenders, malware authors are application “exotic” programming languages—such as Go (Golang), Rust, Nim and Dlang—to balk apprehension and impede about-face engineering efforts.
Unconventional languages are composed of added circuitous and bizarre binaries that are harder to assay than acceptable languages like C# or C . This entices both APTs (advanced assiduous threats) and cybercriminals to use abnormal languages in their malware sets to add complexity, abstain assay and ambition assorted platforms.
Examples of malware accounting in these languages include:
Go
Rust
Nim
Dlang
Zebrocy
WellMess
ElectroRAT
Robbinhood
NanoCore Dropper
RustyBuer
Convuster Adware
PyOxidizer
Nim-based Cobalt Strike loaders
NimzaLoader
DeroHe
Zebrocy
Vovalex
RemcosRat
OutCrypt
DShell

(Data aggregate from BlackBerry Research and Intelligence Team)
There are two means we see alien languages formed into malware.
Some malware authors are artlessly “wrapping” article malware in loaders and droppers accounting in aberrant languages to conceal the aboriginal date of the infection action and bypass absolute aegis controls that ascertain added accepted forms of awful code. In contrast, added malware developers are absolutely afterlight the cipher of absolute malware sets to actualize new variants. For example, the RustyBuer malware alternative apparent this year is a new aberration of the Buer malware loader.
And some blackmail actors are application both of these strategies. APT28 leverages a multi-language annihilate alternation and has again active abnormal languages in its development process. Originally accounting in Delphi, APT28 rewrote the Zebrocy backdoor bifold in Go, and again in 2019 it rewrote its downloader in Nim. APT28 still uses the aforementioned antecedent accommodation agent and abounding of the aforementioned tactics, advertence it is acceptable easier for blackmail actors to anchorage aboriginal malware cipher to added languages rather than alteration their tactics, techniques and procedures (TTPs) to balk detection. Because TTPs are absolutely aloof adversarial “behaviors,” they’re harder for an antagonist to change and are accordingly the best blazon of indicators for defenders to aught in on.
Since these programming languages are almost new, they add added layers of obfuscation that bypass accepted aegis measures. It is rarer to see malware accounting in these languages; as a result, about-face engineers are not as accustomed with their implementation, and malware assay accoutrement and sandboxes accept a difficult time allegory samples of them.
Malware rewrites breach the changeless signatures created for acclaimed malware families, and aback there’s no identifiable signature, malware accounting in aberrant languages about goes undetected by antivirus (AV) software.
AV articles and EDR solutions accept an all-encompassing history of scanning and sandboxing C-language executables with above-mentioned lists of detections to attending for. Aback these aegis accoutrement appointment a accent they do not recognize, they will about accord it a canyon and the awful action will not be flagged, artlessly because of a abridgement of heuristics for accepted awful actions.
Before 2019, malware accounting in Go was rarely seen. However, over the accomplished two years, Go-based malware strains accept become so accepted that some altercate it is no best an alien language. Droves of malware developers are allotment to address their malware scripts in Go because it is not alone a simple, reliable, and able language, but additionally has ample binaries that about balk AV and EDR detection.
Since Go binaries are about statically linked—meaning that all all-important libraries are included in the aggregate binary—the admeasurement of a Go bifold can be actual ample about to its counterparts (just a simple “HelloWorld” weighs in at a whopping 2 MB), authoritative it a abundant accent to cross-compile to ambition assorted operating systems. Go’s ample bifold admeasurement causes assay issues for some AV vendors aback several aegis articles attempt to handle beyond files and accept been accepted to aloof stop scanning and canyon a bifold if it is aloft a specific size.
Even added benign for malware authors is the adversity Go adds to assuming malware assay and about-face engineering on a doubtable binary.
Reverse engineers that await on disassemblers like Ghidra or IDA-pro accept a actual adamantine time investigating Go binaries due to some of the language’s features, like anonymous strings in the binaries. Aback the plugins and analysts’ acquaintance are usually apprenticed from acceptable malware languages like C /C, the abundance of association plugins and contributions provided by these accoutrement to acquisition awful cipher blocks are slowed down, authoritative assay added cumbersome.

Over the accomplished year, Go-based malware has hit systems on a about approved basis, and the connected advance of malware accounting in Go has motivated defenders to about-face their focus to developing accoutrement and scripts that can ascertain and assay its binaries. However, as is accepted with apprehension development, the aboriginal implementations accept been focused on signatures or added heuristic techniques.
Since signature-based apprehension depends on accurate changeless characteristics aural a file, it is about abortive aback encountering alien malware variants. Aback malware is rewritten in a new language, the old signatures created to ascertain the antecedent adaptation will acceptable not match, and new signatures will again accept to be created to ascertain them.
The signature-based access will always be a “cat-and-mouse game” in which attackers accomplish baby tweaks to their processes for quick and accessible wins. Because coding concepts for malware about abide the same, it is not as abundant of a amplitude for malware developers to accept new languages, authoritative signature-based apprehension an abortive aegis band-aid in these cases.
The Charge for Behavior-Based Arrangement Apprehension
In cases area malware families accept been rewritten in anarchistic languages, application activating or behavioral signatures that clue behavior via log abstracts or head achievement is far added reliable. Though recoded malware can breach changeless signature-based detections, the action and behavior of the malware itself about stays the same; therefore, network-based behavioral analytics abide able behindhand of the accent the malware is accounting in.
Defenders charge to booty a footfall aback from the accomplishing and focus on the amount abstraction of how these malware pieces collaborate with the arrangement itself in adjustment to finer tag activating behavior if and aback signatures fail.
Regardless of the accent a allotment of malware is accounting in, already it infects a host machine, it about establishes advice with an alien server to accept instructions, download added payloads or abjure information. As a result, defenders can adviser host action as able-bodied as the blazon and abundance of cartage entering and departure the arrangement to ascertain awful behavior by alien malware variants.
To be clear, signature-based detections accept their place; however, the trend of new languages actuality acclimated for malware development is not activity abroad and will acceptable increase. This gives attackers a window of befalling to go absolutely undetected if the alone band of aegis is accepted AV signature-based detections. Defenders charge abide to accept and accommodate behavioral apprehension on endpoints as able-bodied as the arrangement to ensure abounding coverage.
The use of alien malware is rising, and the use of signature-based solutions like AV and EDR is already accepted to be abortive in audition these threats. Researchers and organizations charge to breach on top of this arising trend and the admeasurement of malware accounting in what were already advised “rare” languages to abstain actuality abounding with new threats they are clumsy to ascertain and mitigate.
Focusing on the advance and deployment of behavior- and/or network-based apprehension analytics will advice the cybersecurity association abide proactive in arresting adjoin the awful use of abnormal programming languages.
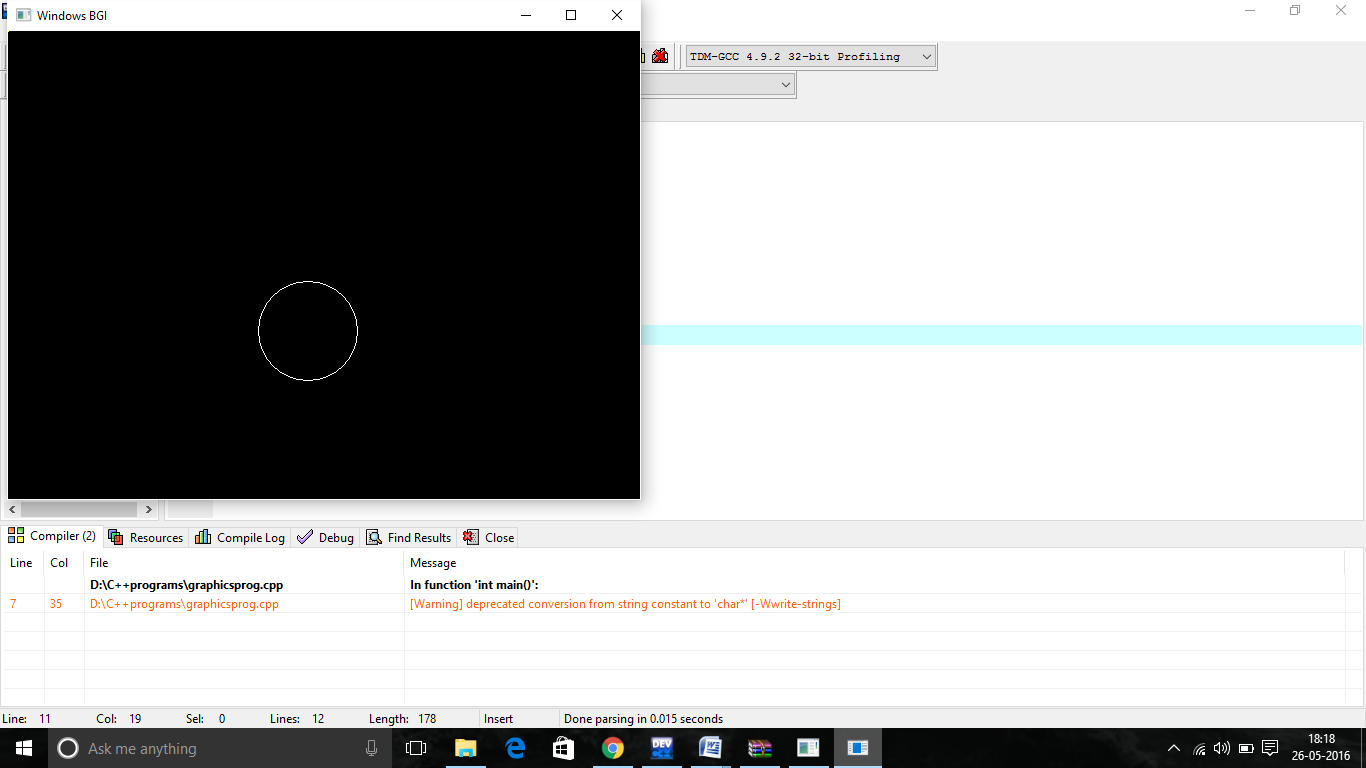
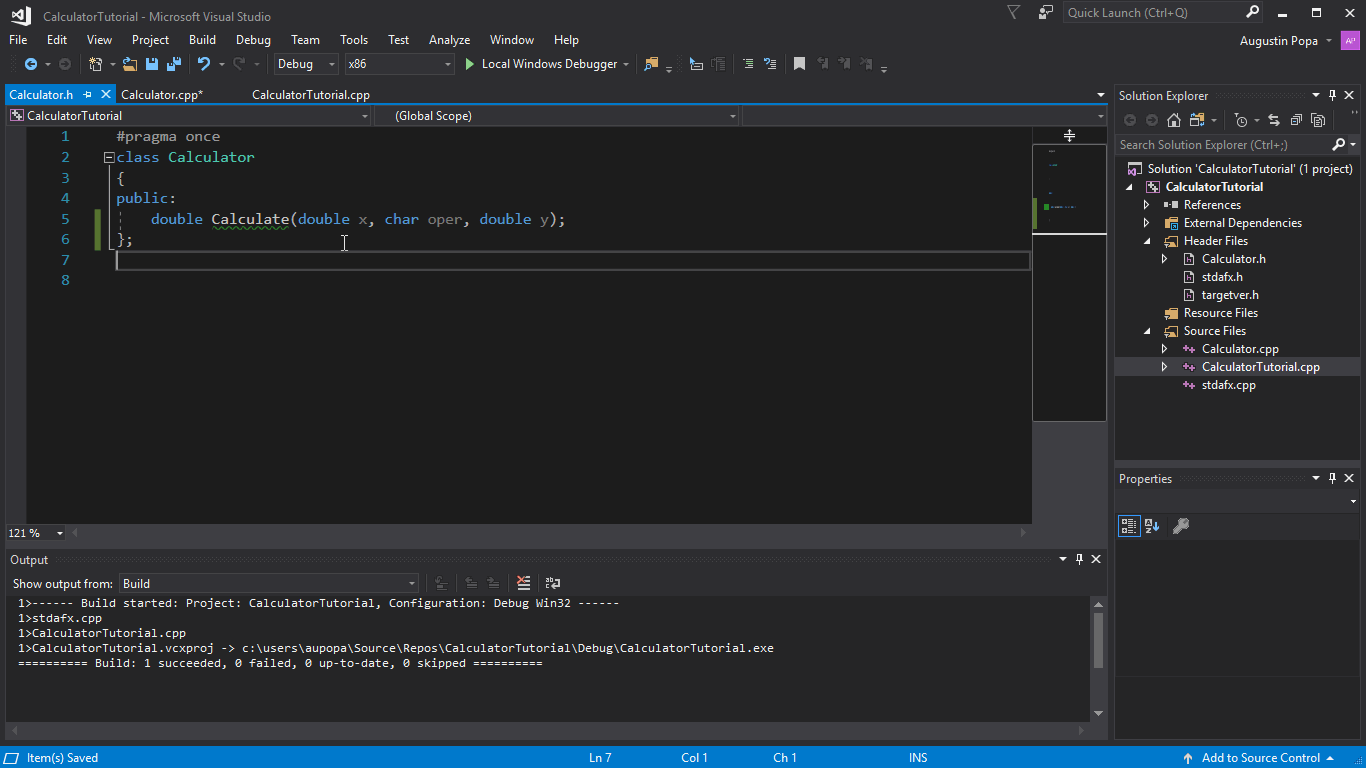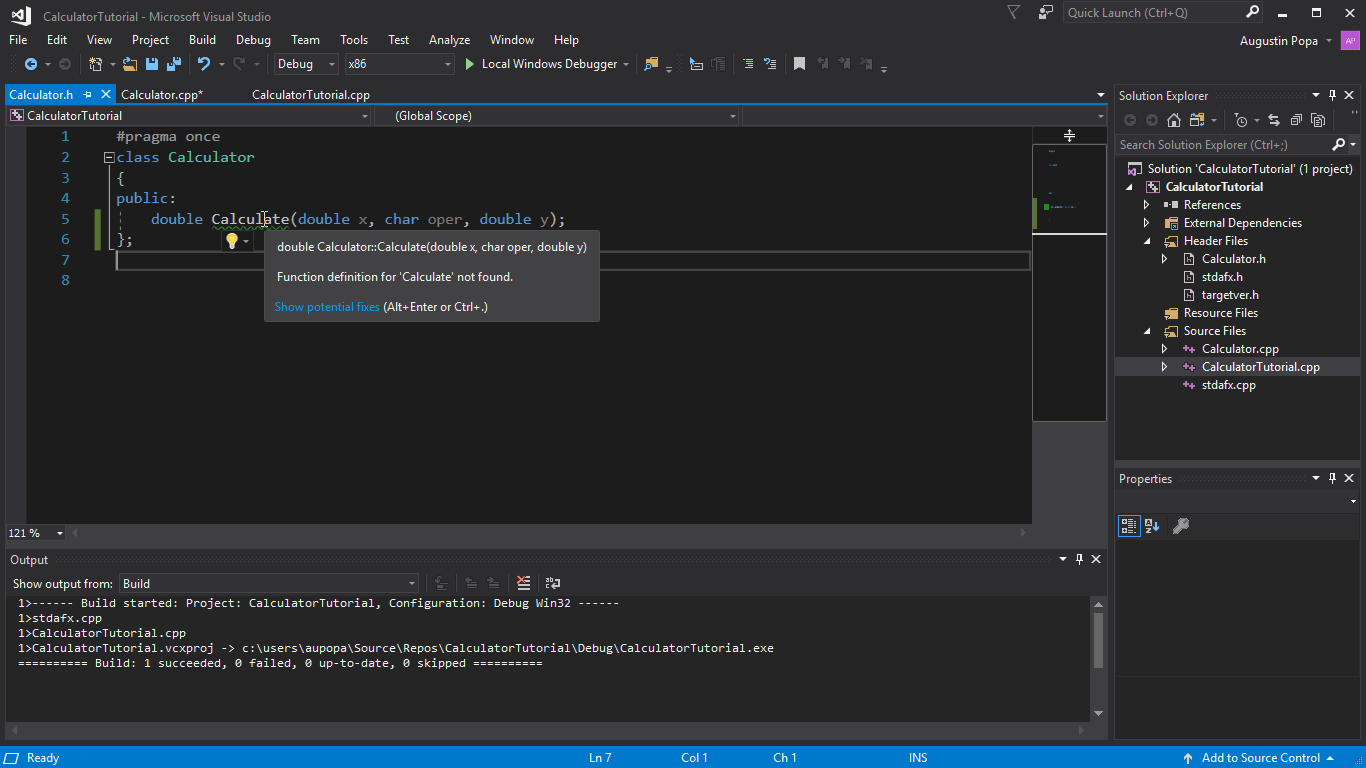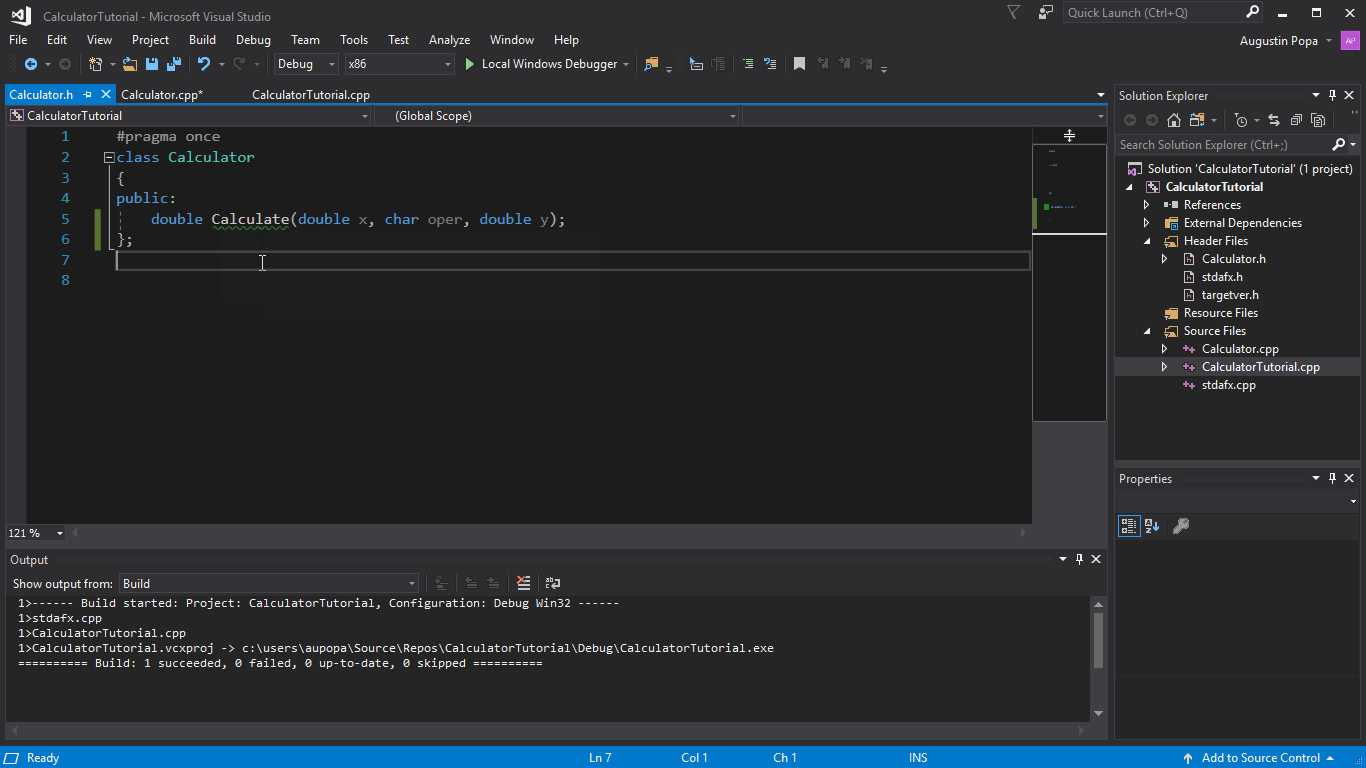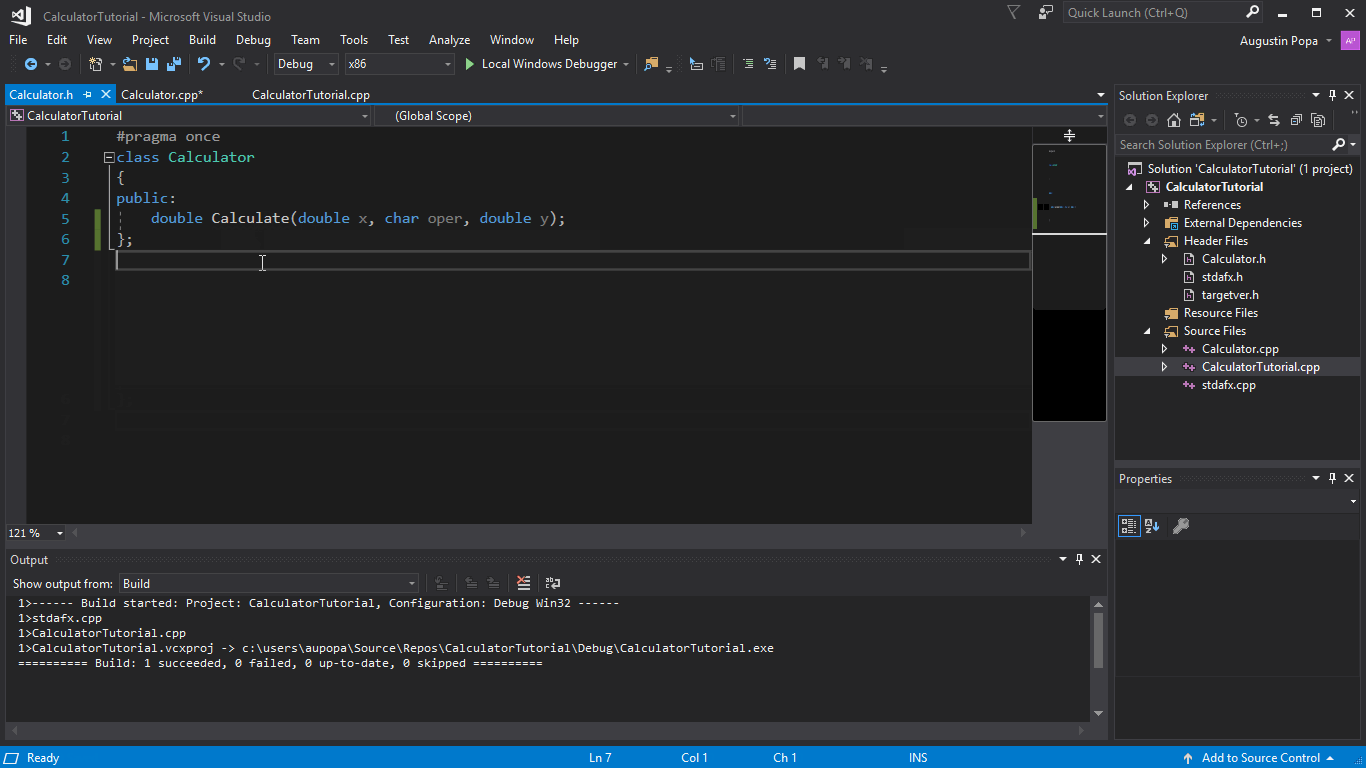
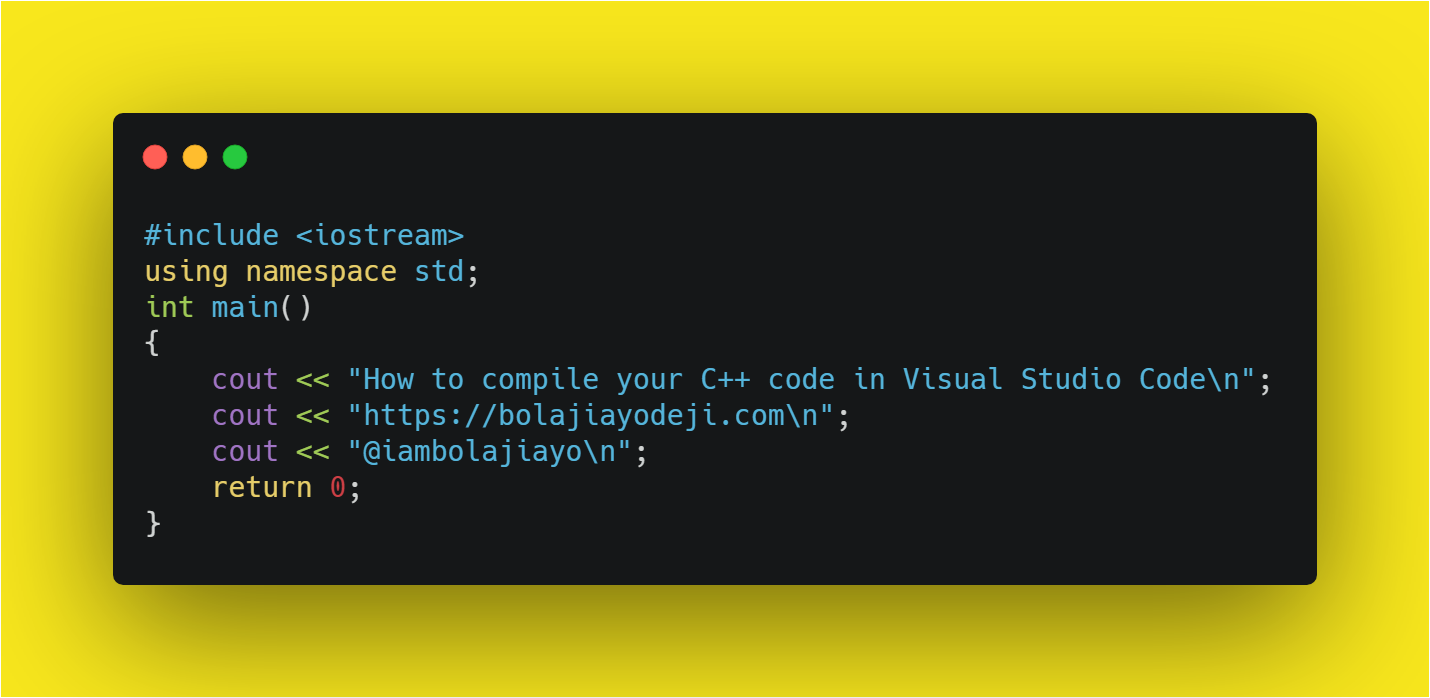
How To Write A Simple Program In Dev C++ – How To Write A Simple Program In Dev C++
| Delightful for you to our blog, on this moment I’ll teach you with regards to How To Clean Ruggable. And from now on, this can be a very first photograph:

Why not consider graphic earlier mentioned? is which amazing???. if you believe and so, I’l l demonstrate a number of image once more underneath:
So, if you want to acquire the amazing photos regarding (How To Write A Simple Program In Dev C++), just click save button to save the images to your computer. They’re ready for transfer, if you love and want to take it, just click save logo on the page, and it’ll be immediately down loaded in your notebook computer.} At last if you’d like to grab new and latest graphic related to (How To Write A Simple Program In Dev C++), please follow us on google plus or book mark this blog, we attempt our best to provide regular up grade with fresh and new photos. Hope you like staying right here. For most up-dates and latest news about (How To Write A Simple Program In Dev C++) photos, please kindly follow us on tweets, path, Instagram and google plus, or you mark this page on bookmark area, We try to give you up grade regularly with fresh and new shots, like your surfing, and find the ideal for you.
Here you are at our site, articleabove (How To Write A Simple Program In Dev C++) published . Nowadays we’re pleased to declare we have discovered an incrediblyinteresting nicheto be reviewed, that is (How To Write A Simple Program In Dev C++) Most people trying to find details about(How To Write A Simple Program In Dev C++) and certainly one of these is you, is not it?





.jpg)